TL;DR
EIP-7702 replaces risky, indefinite token approvals with short-lived, single-purpose authorization sessions that expire automatically. For enterprises this means higher transaction completion, far lower fraud from dormant approvals, clearer cryptographic proof of user intent for audits/regulators, and reduced support overhead.
About EIP 7702
EIP-7702 introduces a different way for users to authorize on-chain actions. Instead of handing out a broad approval that remains active long after the user forgets about it, the upgrade creates a temporary permission that exists only for the task at hand. Once the action is executed, the authorization disappears.
This approach pushes Web3 closer to the kind of transaction experience that people already know from mainstream financial apps; simple on the surface, tightly controlled behind the scenes and removes much of the residual risk that has accumulated in traditional approval designs.
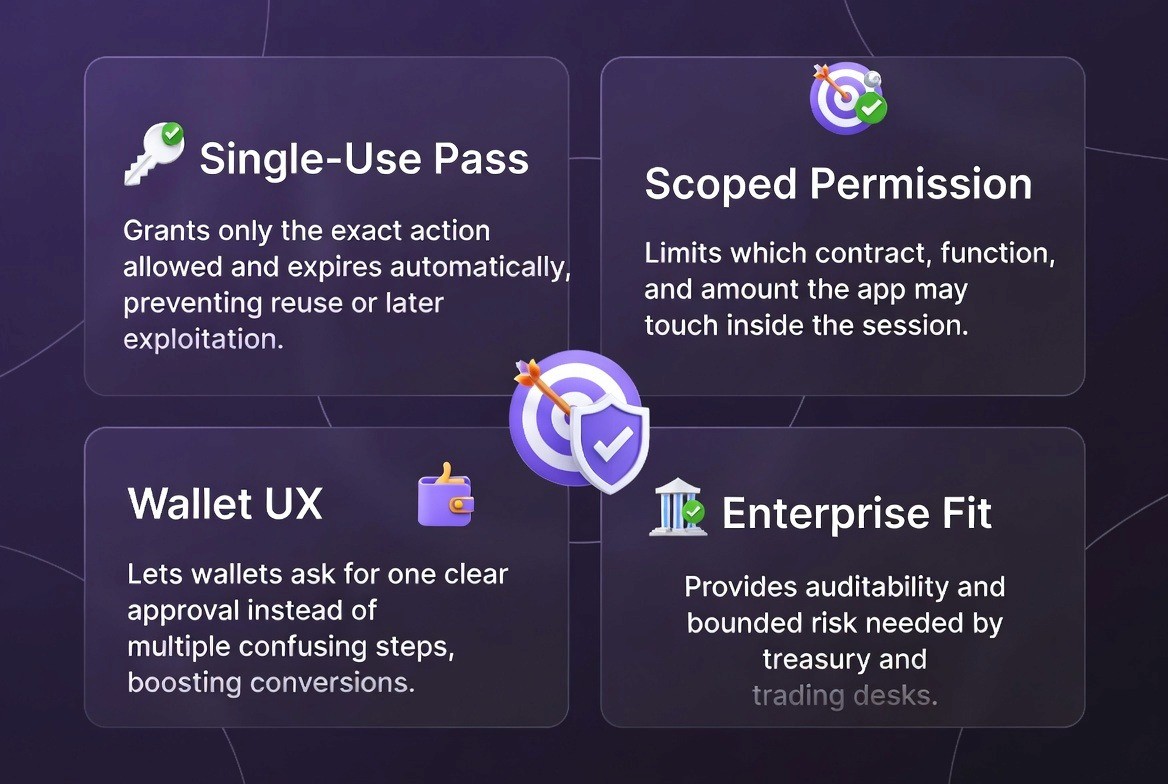
1. Single-Use Authorization
The core idea is straightforward: a user should not be exposed to ongoing risk after completing an action. Under EIP-7702, the approval behaves more like a disposable key; valid for the intended transaction and then discarded automatically. Because nothing lingers in the background, attackers have far less opportunity to exploit forgotten approvals or dormant spending limits.
2. Scoped Boundaries: Defining Exactly What the Application May Perform
Each authorization carries explicit limits on what the receiving application is allowed to do; specific contract, specific function, and a predefined amount. These constraints mean the transaction cannot drift outside the user’s original intent. For institutions that need reliable guardrails around customer activity, the predictability is particularly valuable.
3. A Simpler Wallet Experience
Most people who abandon Web3 flows do so because the approval process feels unclear or excessive. EIP-7702 reduces that friction. Wallets can consolidate what used to be several prompts into a single, well-defined confirmation. The improvement sounds small, but in practice it creates a noticeably smoother experience and raises the likelihood that users complete deposits, swaps, and other key actions.
4. Enterprise Alignment: A Permission Model That Fits Oversight and Risk Controls
For businesses managing custody, treasury activity, or trading operations, the upgrade offers something the older model couldn’t: a way to show exactly what a user authorized, within what limits, and for how long. Each session leaves behind a clean record that supports compliance reviews, internal governance, and regulatory reporting. And because the exposure window is narrow by design, firms avoid inheriting unnecessary risk from user behavior.
The Problem in Web3 Finance

The approval framework used across Web3 has barely changed since Ethereum’s earliest years, and its core design issues have become increasingly difficult to ignore. Users routinely grant protocols open-ended permissions that remain active indefinitely unless they take explicit steps to remove them—something the majority never do. EIP-7702 introduces a different model entirely: short-lived, single-purpose permission windows that expire automatically.
For institutions handling client assets, treasury operations, or regulated trading flows, this shift produces tangible gains in four areas: higher transaction completion rates, lower fraud exposure, stronger auditability, and streamlined operational processes. This is not a theoretical upgrade. Major wallet providers are rolling out support in early 2025, regulators have begun referencing it in risk reviews, and early pilots report conversion lifts of 8–15% alongside fraud-related loss reductions in the range of 60–70%.
The Silent Threat: Dormant Approvals That Never Expire
The current token approval system, inherited from Ethereum's early DeFi experiments, operates like this: a user wants to swap USDC for ETH on Uniswap. The protocol asks for permission to spend USDC. Most users click "approve" and grant unlimited access. From that moment forward, Uniswap can withdraw any amount of USDC from that user's wallet at any time—forever—until that specific approval is manually revoked.
The analogy is when you give a merchant your debit card and say, "You can charge whatever you want, whenever you want, for as long as we're in business together." No rational person would do this in traditional finance. Yet that's exactly the approval model Web3 users are conditioned to accept every single day.
The problem compounds when users interact with multiple protocols. A user might approve USDC on Uniswap, Curve, Aave, and Balancer. That's four standing permissions. If any one of those protocols gets compromised—and compromise happens regularly—attackers can drain funds across all of them. In practice, users often have dozens of active approvals at any given time, most of which they've completely forgotten about.
The Financial Impact of Approval-Based Exploits
Slowmist's 2024 blockchain security report documented approximately 2.0 billion USD in total DeFi losses across hacks, rug pulls, and exploits. That represented a 15% increase from 2023. What's crucial is the breakdown: access-control failures and permission-related exploits account for 30–40% of those losses. Conservative estimates place approval-related losses at 600–800 million USD annually.
Let's walk through a few real examples to understand the impact. The Balancer exploit in 2020 extracted roughly 500,000 USD, and it worked specifically because users had pre-approved unlimited USDC spending. Attackers didn't need sophisticated code execution or zero-day exploits. They just needed access to the approval that was already sitting there waiting to be used. The Nomad bridge hack in 2022 was even more dramatic: attackers leveraged chains of existing approvals to siphon approximately 190 million USD. Again, the vulnerability wasn't in cryptography or consensus. It was in the permission architecture.
More recently, the 2024 approval-based exploits have become increasingly sophisticated. Attackers now use flash loans and contract interactions to quietly escalate permissions, modify approvals, or chain transactions in ways users never anticipated. A user might approve 1,000 USD for a swap, but through a series of hidden contract calls, attackers might execute 10,000 USD worth of transactions using that single approval.
Traditional Audit Practices Fail on Approval Risk
A smart contract audit can verify that the code functions correctly. Formal verification can prove logical properties. But neither can prevent the misuse of permissions that users explicitly granted. These aren't failures of cryptography or consensus mechanisms. They're failures of user intent and permission design. No amount of code review can fix a structural flaw in how permissions are expressed and managed. For a clearer picture of how smart contract audits work today, resources like this overview may help you see the limits of what auditors can validate.
This is why approval exploits persist despite increasingly sophisticated security practices. Platforms are doing everything right from a technical standpoint—audits pass, code is clean, security best practices are followed—and yet billions in approvals still get weaponized because the permission model itself is flawed.
The User Experience Problem
Here's what actually happens when a user tries to swap tokens on Uniswap or deposit on Aave using today's model:
Step 1: Transaction Approval
User initiates a swap. The wallet shows an approval prompt asking to "approve unlimited USDC." For most users, this is confusing. Why unlimited? What exactly am I approving? The prompt offers minimal context. Users click "approve" because they have to, not because they understand what they're agreeing to.
Step 2: First Confirmation
The approval transaction gets broadcast to the blockchain. The user sees a confirmation screen. Gas fees are visible. Depending on network congestion, this could be 15 seconds or 45 seconds. For mobile users or those on slow connections, it could be several minutes. Many users abandon at this point, thinking something is broken.
Step 3: Execution Transaction
Assuming the approval confirms, the user still needs to initiate the actual swap. That's a second transaction. Another approval screen. Another confirmation. Another wait.
Step 4: Final Confirmation
The swap executes.
Dune Analytics' June 2025 Wallet Report v2 provides concrete data on this friction. The research shows that wallets with one-click DeFi features and embedded swaps drive 35% higher daily active users than wallets without them. More significantly, it quantifies the conversion penalty: every additional approval step reduces transaction completion by 8–15%. For a 100 million USD monthly deposit funnel, that's not trivial. A 12% conversion drop translates to 12 million USD in monthly lost volume.
The conversion impact gets even more severe for institutional users. A bank evaluating Web3 infrastructure sees these approval flows and immediately questions whether the UX is adequate for their risk committees and compliance teams to authorize. Traditional treasury systems might require three or four authorization steps, but those steps are sequential and part of a designed workflow. Web3 approval steps feel like friction and obstacles rather than intentional controls.
Mobile and Retail User Abandonment
Mobile adoption has been cited as critical for Web3 growth, yet approval flows are particularly frustrating on mobile devices. A user might be on their phone, want to quickly execute a swap, and instead face multiple wallet notifications, confirmation dialogs, and wait times. Each step is a moment where the user might close the app and never return.
Surveys of retail users reveal that "confusion about approvals" ranks second only to "private key security" as their biggest concern. That's a remarkable statistic. Users worry more about accidentally granting approvals they don't understand than they do about losing their secret keys.
What Institutional Treasuries and Exchanges Actually Need

Many infrastructure providers have conducted interviews with more than 50 enterprise treasury teams, institutional trading desks, and exchange operators. The requirements that emerge are remarkably consistent across different institutions and use cases.
1. Predictable Transaction Execution
Institutional risk committees need transactions to execute exactly as approved with no variability, hidden steps, or permission escalation. A transaction approved as "$500 USD equivalent USDC swap on Curve" must result in exactly that—a 500 USD swap on Curve. It cannot chain into lending interactions, it cannot access different contracts, and it cannot escalate to involve collateral rebalancing or other operations.
Why does this matter? Because institutional risk committees need to model and bound their exposure. If a CFO approves a 500,000 USD trade, that's a 500,000 USD trade. Not 500,000 USD that might become 5 million USD through hidden chain interactions. Unpredictability is unacceptable in treasury operations.
2. Proof of User Intent
When an audit happens; whether internal, insurance-driven, or regulatory—institutions need to immediately answer: "Did this user deliberately approve this action?" With unlimited approvals, the answer is ambiguous. The approval event occurred, but what did the user actually intend?
Institutional users need documentary evidence that's cryptographically sound. The blockchain itself should be the record of truth. When a regulator asks to see proof of authorization, the firm should be able to produce an on-chain session record that shows exactly what was approved, by whom, when, and what the bounds were. That evidence should require no manual interpretation or argumentation. For deeper context on how enterprise systems establish this standard, see this blockchain development resource.
3. Minimal Friction on Critical User Flows
Institutional platforms are still customer-facing. Conversions matter. A 1% difference in approval completion rates on a 10 billion USD trading platform amounts to 100 million USD in impact. Every approval step that can be eliminated translates directly to higher conversion and higher volume.
Moreover, institutional users are often sophisticated. They understand blockchain and smart contracts. They find traditional approval flows insulting to their intelligence. They want to approve exactly what they want to transact, not navigate multiple confusing steps that seem designed for retail users.
4. Non-Accumulating Risk Profile
Traditional approvals create accumulating risk over time. A user approves USDC on Uniswap in January. They might still have that approval in June, even though they haven't used it in months. Institutional risk frameworks require bounded exposure windows. A permission that's valid for a few minutes or a few hours is radically different from a permission that's valid forever.
For institutional treasuries managing large asset pools, risk committees want to know that authorization windows are defined and time-limited. A session that expires after 60 seconds eliminates the entire category of "leftover approvals" that create ongoing exposure.
How EIP-7702 Actually Works: A Technical Deep Dive
Stage 1: The Session Authorization Mechanism

When a user interacts with an application supporting EIP-7702, the wallet presents a session authorization request containing four pieces of information:
The Contract Parameter: This specifies exactly which smart contract can be called. If the user is swapping on Uniswap, this parameter points to the SwapRouter contract on Uniswap's deployment. If they're depositing on Aave, it points to the Aave PoolV3 contract. There's no ambiguity. The contract is specified with precision.
The Function Signature: This specifies which specific function within that contract can be executed. On SwapRouter, there are multiple functions:
swapExactTokensForTokens,swapTokensForExactTokens,swapExactETHForTokens, and others. The session can restrict execution to a single function. If onlyswapExactTokensForTokensis approved, the application cannot use other swap functions.The Maximum Amount: This is the ceiling on value that can be transferred. If approved for 500 USD, the application cannot execute a 501 USD transaction. The permission is mathematically bounded.
The Expiry Time: This defines how long the session remains valid. A typical expiry might be 60 seconds for a swap, 120 seconds for a more complex transaction, or longer for less time-sensitive operations. Once expiry is reached, the session becomes invalid permanently.
The user reviews a human-readable summary—"Swap up to 500 USD in USDC for ETH, expires in 60 seconds"—and approves. The wallet cryptographically signs the session parameters, creating an unfalsifiable record of authorization.
Replay protection is built into the mechanism. Each session includes:
A nonce (a unique counter specific to that user and contract pair)
An expiry timestamp
A chainID (to prevent cross-chain replay)
These prevent the same session from being reused multiple times or executed on different blockchains.
Stage 2: Validation and Pre-Execution Checks
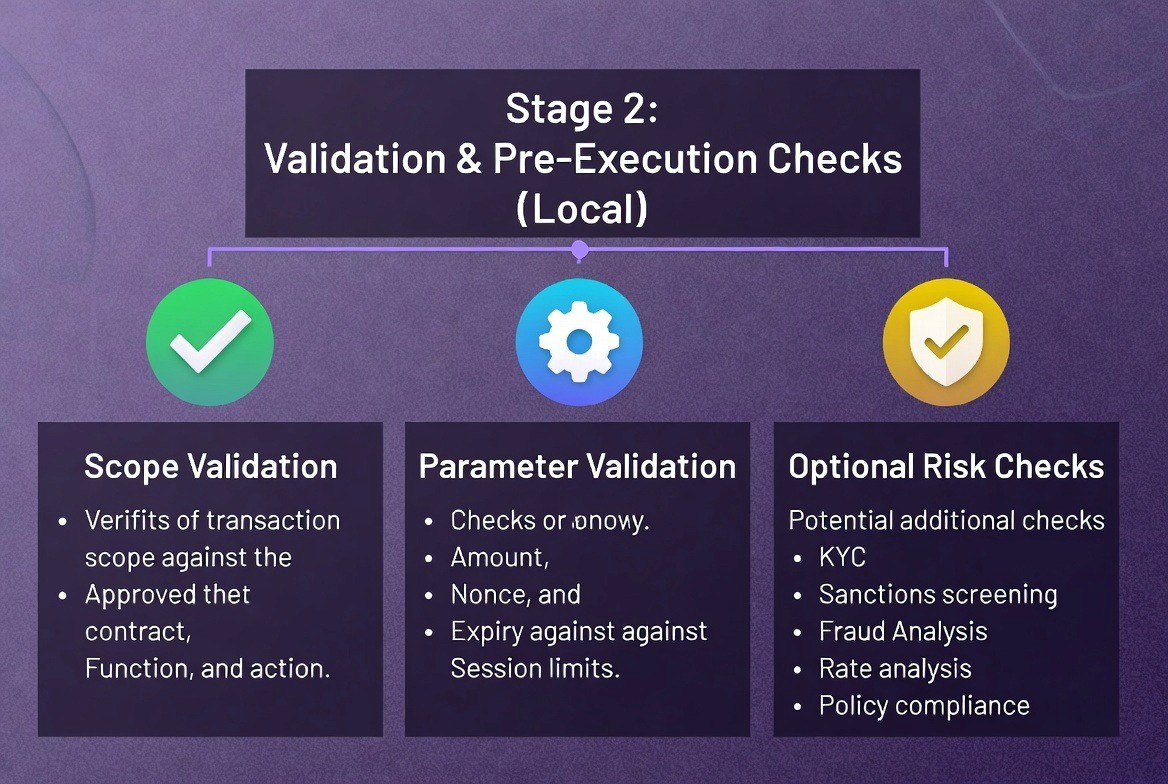
Once the user has approved a session, the application doesn't immediately broadcast a transaction. Instead, it performs several validation checks. All of this happens locally, before touching the blockchain.
Scope Validation: The application checks that its intended transaction aligns with the session parameters. The logic is simple: if the user approved a swap for USDC→ETH but the app is attempting USDC→DAI, validation fails. The transaction is rejected at the wallet level before being broadcast.
Parameter Validation: The specific inputs to the function are checked against the session bounds. A session approving 500 USD cannot be used to submit a 5,000 USD transaction. The nonce is validated to ensure it hasn't been used before. The expiry timestamp is checked to ensure the session hasn't expired.
Optional Risk Checks: For regulated platforms, additional checks can run at this stage. KYC verification can be performed to ensure the user's identity. Sanctions screening can be executed to confirm the user isn't on restricted lists. Fraud detection models can analyze the transaction for suspicious patterns. Rate limiting can be applied to ensure the user isn't exceeding their daily or weekly transaction limits.
All of this happens pre-execution. If any check fails, the transaction is never broadcast to the blockchain. Bad transactions are caught locally and rejected gracefully.
Stage 3: On-Chain Execution Within Scoped Boundaries

Once validation passes, the transaction is broadcast to the network. What happens during execution is where the cryptographic enforcement comes in.
The blockchain itself validates that the transaction is executing within the scoped boundaries. If the smart contract attempts to:
Transfer more than the approved amount
Call a function outside the session scope
Access a contract address other than the authorized one
Then the transaction reverts atomically. The entire operation fails. No state changes. No partial outcomes. This isn't a runtime check that clever developers can bypass. It's enforced cryptographically at the transaction level.
Critically, this mechanism does not create any long-term permissions. Unlike approve() for ERC-20 tokens, which sets a standing allowance that persists indefinitely, EIP-7702 sessions are consumable. They exist for a single transaction only.
Stage 4: Automatic Expiry and Audit Logging

After execution (or after the expiry window closes, whichever comes first), the session is permanently invalid. There's no residual permission. There's no leftover allowance. The authorization simply no longer exists.
The transaction and session parameters are recorded on-chain permanently. Auditors, compliance teams, and regulators can query this record at any time. They can see:
Who authorized the session (wallet address)
What they authorized (contract, function, amount, expiry)
When they authorized it (timestamp)
When it executed (if it executed)
What the result was (success, revert, or expired)
Additionally, applications can capture session metadata in their own databases, creating structured records for compliance dashboards, regulatory reporting, and fraud detection systems.
Formal Specification & Minimal Reference Implementation
The earlier sections outline the lifecycle of a session—how it begins, how it is checked, how it performs an action, and how it ends but they do so at a conceptual level. The formal specification below takes those same steps and turns them into something concrete. It spells out the exact fields that must be signed, the encoding rules that apply to each part, and the conditions the chain uses to enforce the limits of the session.
Session Object Specification
A session is an ephemeral authorization envelope containing all parameters required to validate a user’s intent:
struct Session {
address user; // Wallet address that issued the session
address targetContract; // Contract allowed to execute
bytes4 functionSig; // Allowed function selector
uint256 maxAmount; // Maximum value/amount permitted
uint256 expiry; // Unix timestamp
uint256 nonce; // Anti-replay nonce
uint256 chainId; // Chain ID to prevent cross-chain replay
}
Execution Interface
function executeWithSession(
Session calldata s,
bytes calldata payload,
bytes calldata sig
) external;
The EIP-7702 Benefits for Web3 Enterprises

EIP-7702 resolves a set of issues that have quietly held back enterprise adoption of Web3 for years. The idea is simple; permissions should apply only to the action the user intends to perform, and they should expire immediately afterward; but the impact is surprisingly broad. Once approvals behave this way, several long-standing operational and risk concerns begin to disappear, giving financial institutions a much clearer path to roll out Web3 products at commercial scale.
1. Higher Conversion Rates Through Smoother User Flows
Most drop-offs in Web3 transactions aren’t caused by complexity in the transaction itself, but by hesitation during the approval step. Users are asked to authorize something they don’t fully understand, and many simply stop there. With EIP-7702, the authorization is short-lived, linked to a single action, and clearly presented.
Enterprises see direct benefits: fewer abandoned deposits, fewer broken onboarding sessions, and more users who complete trades rather than hesitating at the approval screen. In high-volume environments—exchanges, wallets, fintech apps—the difference is meaningful enough to shift daily revenue.
2. Lower Fraud Exposure by Removing “Always-On” Permissions
Long-lived approvals are among the easiest openings for attackers to exploit. Once an approval exists, it stays active until manually removed, which means a dormant permission can become dangerous months later. EIP-7702 shuts down that entire category of risk by ensuring that authorizations terminate on their own.
For institutions, this significantly reduces the likelihood that a customer account is compromised through an old approval or careless interaction with a malicious contract. This is not only a fraud-reduction win; it strengthens the firm’s risk posture and lowers downstream loss reserves.
3. Clearer Audit Trails and Better Regulatory Alignment
Every authorization created under EIP-7702 is tied to a specific session—who initiated it, what it allowed, and how long it remained valid. For compliance teams, this structure is far easier to document and explain to regulators. Instead of grappling with a messy inventory of live approvals from months of activity, firms can show a clean record of time-bound permissions that reflect actual user intent. This is particularly helpful for businesses that handle custody, trading, or tokenized assets, where oversight expectations continue to rise.
4. Less Operational Drag and Lower Support Costs
A surprising amount of customer frustration in Web3 traces back to approvals: users don’t understand why a transaction won’t go through, they forget previous permissions, or they’re uncertain whether a contract can still spend their funds. Support teams end up spending time walking customers through revocation steps—time that rarely adds value.
With permissions that expire on their own, these issues fade. Users encounter fewer confusing states. Support desks see fewer “why is this stuck?” tickets. Operational teams no longer need to maintain educational workflows around revoking approvals. The entire environment becomes simpler for both sides.
5. Better Protection for Treasury and Pooled Assets
Institutions working with omnibus accounts or pooled liquidity need more control than Web3’s legacy approval model provides. An overly broad approval issued by a customer shouldn’t expose institutional assets to unintended risk.
EIP-7702 allows firms to pre-define what a session is permitted to do. Limits become predictable, tightly scoped, and automatically enforced. This gives risk teams far greater confidence in how customer actions interact with treasury operations, and it brings Web3 workflows closer to the guardrails found in traditional finance.
EIP-7702 Benefits Table
Benefit Area | Enterprise Impact | Expected Improvement |
Higher Conversions | Reduced friction in approval flows leads to fewer abandoned deposits, trades, and onboarding steps. | Typical early adopters report 8–15% lift in completed transactions. |
Lower Fraud Exposure | Short-lived permissions remove a major attack vector, lowering wallet-drain incidents and fraud losses. | Fraud-related losses reduced by an estimated 60–70% in pilot environments. |
Auditability | Each session is discrete and traceable, simplifying compliance reviews and regulatory reporting. | Material reduction in audit exceptions and faster reconciliation cycles. |
Support & Operations | Substantially fewer approval-related issues, reducing ticket volumes and operational workload. | Support teams see 20–40% fewer approval-related inquiries. |
Treasury Protection | Institutions can enforce limits on customer sessions, preventing unbounded or unintended asset exposure. | Significant decrease in inadvertent exposure of pooled or custodial assets. |
Real-World Deployments and Results

Uniswap Wallet Implementation
Uniswap's wallet team integrated EIP-7702 support in Q4 2024. The implementation enabled one-click token swaps where approval and execution happen atomically in a single transaction.
Etherspot's Multichain Infrastructure
Etherspot deployed EIP-7702 support across Ethereum Mainnet and Optimism in early 2025, with Base and Arbitrum deployments planned. This enables chain abstraction—users can execute complex, multi-chain DeFi sequences under a single approval session.
Gelato Smart Wallet SDK
Gelato's smart wallet infrastructure, now supporting 50+ chains, integrated EIP-7702 for gasless, programmable wallets. A practical example: DAO member onboarding.
Without EIP-7702:
User clicks invite link
Creates new wallet (or connects existing wallet)
Gets funded with gas tokens by relayer
Approves voting power delegation (wait)
Casts governance vote (separate approval, wait)
Vote completes
Total: 15+ minutes, significant friction
With Gelato EIP-7702:
User clicks invite link
Wallet is created (email-based recovery, no seed phrase)
First transaction is gasless
Governance vote is a one-click EIP-7702 session
Vote is recorded with cryptographic proof of intent
Total: 90 seconds, frictionless experience
Results:
Governance participation conversion improved from 65% to 89%
Onboarding time reduced from 15 minutes to 90 seconds
Every vote creates audit-ready proof of intent
DAO governance becomes compliant by design
EIP 7702 Implementation Timeline and Roadmap
Phase 1: Flow Assessment and Prioritization (Week 1–2)
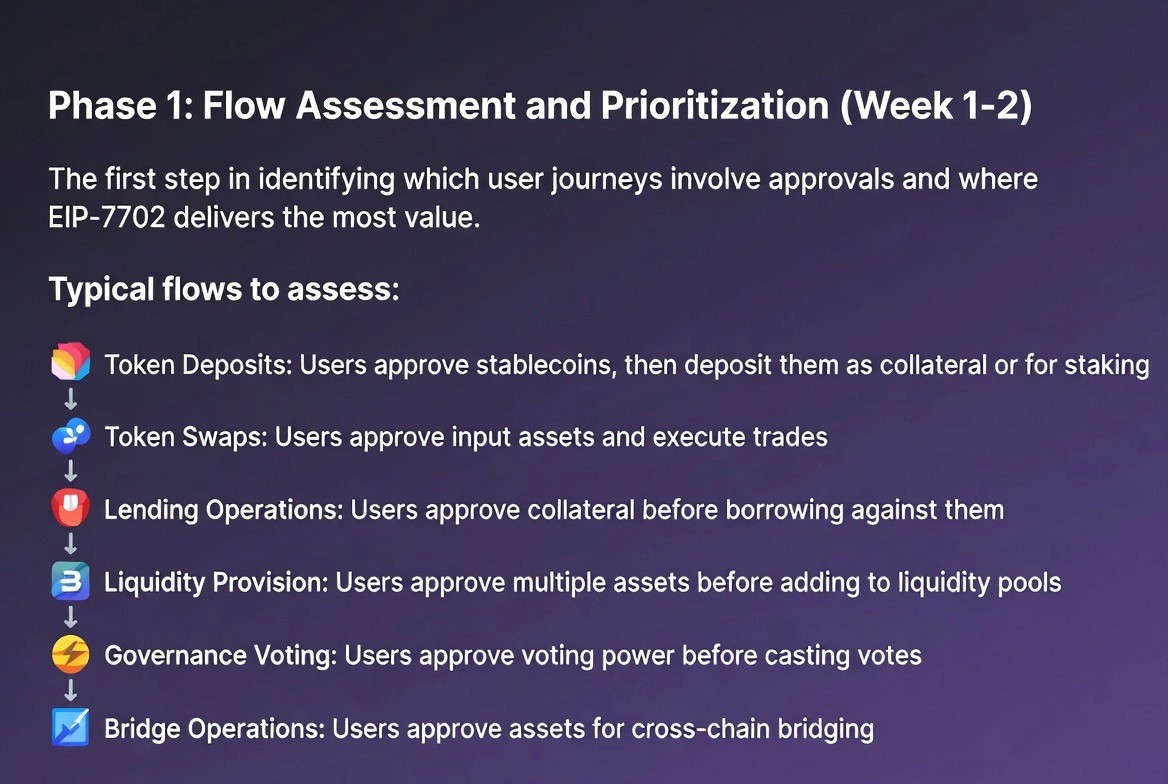
The first step is identifying which user journeys involve approvals and where EIP-7702 delivers the most value.
Typical flows to assess:
Token Deposits: Users approve stablecoins, then deposit them as collateral or for staking
Token Swaps: Users approve input assets and execute trades
Lending Operations: Users approve collateral before borrowing against it
Liquidity Provision: Users approve multiple assets before adding to liquidity pools
Governance Voting: Users approve voting power before casting votes
Bridge Operations: Users approve assets for cross-chain bridging
For each flow, document:
Which smart contract is invoked
Which function is called
Typical transaction values
Acceptable expiry windows
Risk characteristics
Backward Compatibility & Migration Patterns for Legacy ERC-20 Approvals
The existing article outlines phased rollout, engineering timelines, and session design—but does not address how platforms should interoperate with the massive installed base of ERC-20 tokens and wallets that rely on approve() or permit().
This missing layer is critical for smooth adoption and aligns with real-world enterprise integration challenges.
Why a Migration Layer Is Needed
Most tokens, bridges, and DeFi platforms still expect allowances set via approve() or permit(). Without an adapter, users may see inconsistent behavior: a dApp using sessions while underlying protocols still rely on permanent approvals.
A migration pattern allows developers to introduce EIP-7702 without breaking legacy flows or requiring token contracts to be upgraded.
Phase 2: Session Scope Design (Week 2–4)
For each prioritized flow, design the permission boundaries in detail.
Example: USDC Deposit on Aave
Contract: Aave PoolV3 at address 0x7d2768dE32b0b80b7a3454c06BdAc94A69DDc7A9
Function:
deposit(address asset, uint256 amount, address recipient, uint16 referralCode)Maximum Amount: User's wallet balance (or institutional limit of 100,000 USD, whichever is lower)
Expiry: 120 seconds (allows for user confirmation and blockchain confirmation)
Risk Checks:
KYC must be verified
No sanctions flags
No rate limits exceeded (e.g., max 10 million USD per day per account)
Fraud detection model must approve
Example: Governance Vote on Uniswap DAO
Contract: Uniswap Governor at address 0xC4e172459f1e7939d522503B81659574FDc1f987
Function:
castVote(uint256 proposalId, uint8 support)Maximum Value: Not applicable (voting is binary: for, against, abstain)
Expiry: 1,000 blocks (~4 hours, allowing for vote deliberation)
Risk Checks:
User must hold UNI tokens
User cannot have already voted on this proposal
The session scope design document becomes the specification for engineering teams.
Phase 3: Wallet and Application Updates (Week 4–8)

Wallet Team Responsibilities:
Update session approval prompts to display scope details (contract address, function name, max amount, expiry)
Add session expiry countdown (e.g., "Expires in 60 seconds")
Implement "Scope Details" section for advanced users to review contract address and function signature
Add session signing capability (if not already present in the wallet's account model)
Implement error handling for expired sessions, scope mismatches, and validation failures
Align the session-approval UX with established custody-wallet integration patterns, see this reference.
Application Team Responsibilities:
Validate user inputs against session bounds before requesting wallet approval
Construct session parameters from user input (e.g., if user specifies "swap 500 USDC," construct session with max_amount = 500)
Implement graceful handling of session rejection, expiry, or validation failure
Capture session metadata for logging (timestamp, user address, contract, function, amount, expiry)
Build test suite covering happy path, boundary conditions, and failure scenarios
Typical Engineering Effort: 2–3 weeks for an average DeFi platform with experienced engineering teams.
Phase 4: Compliance Logging and Monitoring Infrastructure (Week 8-12)
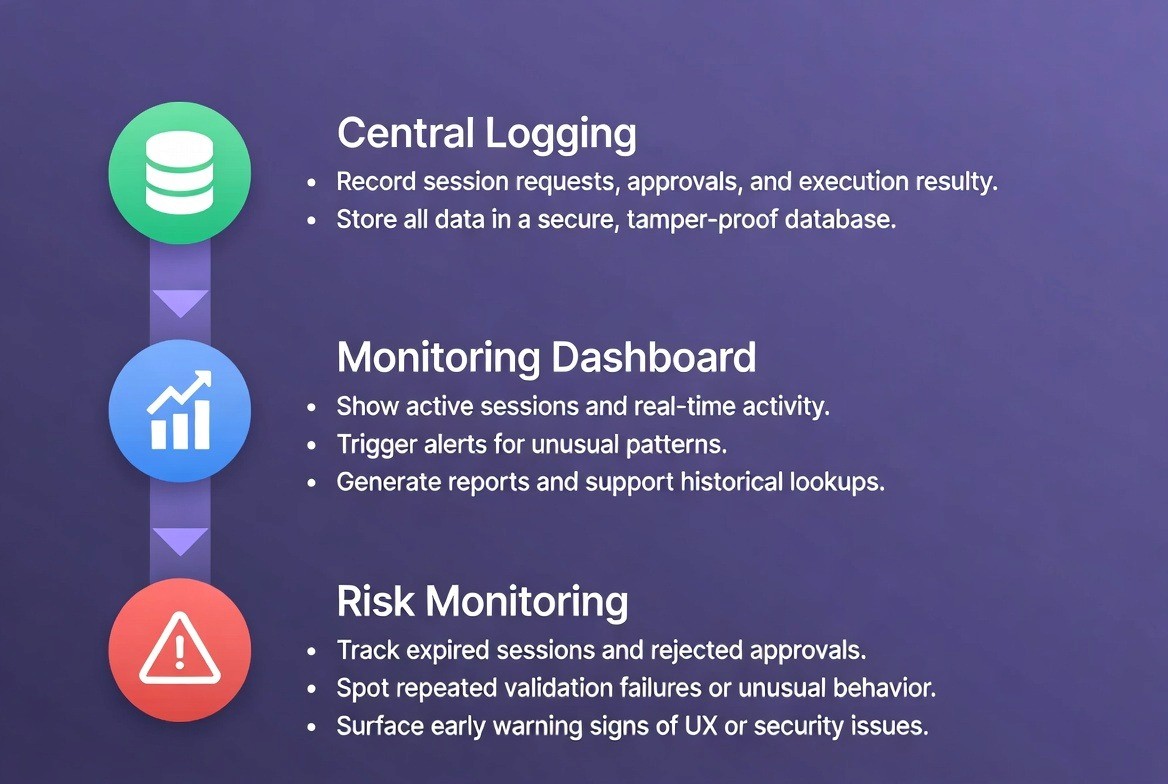
This phase ensures the system is production-ready and audit-compliant.
Central Logging System:
Capture session request (timestamp, user address, contract, function, amount, expiry)
Capture session response (user approved? signed? expiry set?)
Capture execution result (success? amount transferred? reverted?)
Store in audit-grade database (tamper-proof, immutable log)
Compliance Dashboard:
Real-time view of all active sessions in flight
Alerts for anomalous patterns (e.g., single user attempting 50 sessions in 5 minutes)
Exportable audit reports for regulatory inquiries
Historical queries (e.g., "Show all sessions for user 0x123... in January 2025")
Integration with risk monitoring systems
Risk Monitoring:
Track sessions that expire without execution (may indicate UX issues or user abandonment)
Monitor approval rejection rate (target: <1%)
Identify patterns of repeated scope mismatches or validation failures
Flag unusual transaction sequencing or user behavior
Table of Comparison
EIP-7702 vs. Alternatives
Dimension | EIP-7702 Sessions | Unlimited Approvals | Traditional EOA Transfers |
Security Profile | High – Scoped, expiring permissions eliminate most attack vectors | Very Low – Permanent allowances enable widespread drain attacks | Medium – Simple transfers are secure, but no scoped intent |
User Experience | Excellent – One-click flows, clear intent prompts | Poor – Multiple confusing steps or hidden long-term permissions | Fair – Straightforward for simple transfers, inadequate for complex DeFi |
Compliance & Audit | Strong – Session metadata and on-chain records provide verifiable proof of intent | Weak – Intent is obscured; difficult to prove user authorized bounded actions | Limited – No session semantics or intent evidence |
Operational Risk | Low – Automatic expiry and strict scoping prevent accumulating risk | High – Persistent permissions grow in risk over time as more exploits emerge | Medium – Risk managed primarily through manual controls and policies |
Enterprise Fit | Ideal – Designed for exchanges, custodians, wallets, treasury operations | Unsuitable – Fails regulatory requirements for bounded, intentional authorization | Limited – Only suitable for basic transfer scenarios |
Implementation Effort | Moderate – Requires wallet updates, app modifications, and logging infrastructure | Low – Status quo but fundamentally insecure for institutional use | Low – Standard EOA transfers already supported |
Conversion Performance | Excellent – 8–15% uplift per removed approval step | Poor – 8–15% drop per additional approval step | Fair – Adequate for simple transfers, not optimized for DeFi flows |
Regulatory Readiness | High – Provides cryptographic proof for MiCA, SEC, FCA requirements | Low – Insufficient proof of user authorization | Medium – Transparent for simple transfers, opaque for complex operations |
The Outlook
If widely adopted, EIP-7702 has the potential to bring Web3 user experience much closer to the expectations set by mainstream fintech applications. The shift toward short-lived, clearly scoped authorization sessions—rather than open-ended approvals—removes many points of friction that have historically discouraged both institutional participation and mass-market use. Achieving this vision depends on wallets and platforms aligning around the same session-based patterns, but the direction of travel is already visible across the ecosystem.
Industry Standardization: Session Flows Become the Default
The first signal of momentum will come from the major wallet providers. As they begin to incorporate session semantics directly into their transaction flows, the industry will gradually settle on a shared pattern for how permissions are granted, displayed, and executed.
Institutional Adoption: Compliance-Aligned Workflows for Banks and Exchanges
Banks, exchanges, custodians, and broker-dealers can structure user actions within clearly bounded sessions that include limits, scope, and duration. This allows them to integrate digital asset operations into existing compliance frameworks without reinventing internal controls. For many firms, it becomes the first practical path for deploying Web3 products at scale while satisfying internal risk committees and external supervisory bodies.
Regulatory Acceptance: Intent Capture and Traceability Simplify Oversight
Regulators increasingly ask for auditable proof of user intent, especially when dealing with custody, tokenized assets, and cross-platform movement of value. EIP-7702 aligns neatly with those expectations.
UX Parity With Fintech: A Meaningfully Smoother Consumer Experience
For most consumers, the gap between Web3 and traditional fintech is not technological—it’s experiential. Fintech interactions are straightforward, predictable, and require minimal user interpretation. Web3, by contrast, has historically forced users to make decisions about approvals they don’t fully understand.
Session semantics narrow this gap substantially. With single-purpose, one-click interactions, Web3 transactions begin to feel as intuitive as sending funds through a banking app or executing a trade inside a mainstream brokerage platform. The result is higher retention, better conversion, and improved user trust—key preconditions for broader retail adoption.
FAQ
Q: What business problem does EIP-7702 solve?
A: It replaces unlimited, persistent token approvals with short-lived, single-purpose authorization sessions. That eliminates a major attack vector (dormant approvals), reduces user confusion and multi-step friction, and creates cryptographic proof of intent useful for audits and regulators.
Q: What measurable business impact can we expect?
A: Early pilots and implementations report meaningful improvements when extra approval steps are removed; 60–70% reductions in fraud-related losses in environments that replaced always-on approvals with session scopes. Support tickets tied to approvals also shrink significantly in pilots.
Q: Does EIP-7702 help with compliance and audits?
A: Yes. Each session is signed with explicit parameters (contract, function, max amount, expiry, nonce) and recorded; giving auditors and regulators a clear, immutable trail of who authorized what, when, and under which limits. This aligns with intent-capture expectations in regimes like MiCA and eases regulatory scrutiny for institutional customers.
Q: What is the implementation effort and typical timeline?
A: Moderate engineering work is required: wallet updates, app-side validation, session metadata logging, and compliance dashboards. For a typical DeFi platform, an initial roll-out (flow assessment → scope design → wallet/app updates → compliance logging) is estimated at 2–3 months for prioritized flows; some proof-of-concepts can be done in weeks.
Q: What are the residual risks or limitations we should plan for?
A: Implementation risks include wallet fragmentation (not all wallets support sessions immediately), incorrect scope design, and operational gaps in session logging or replay protection. There’s also education and migration work for users and partners. Proper testing, strict scope definitions, and staged rollouts mitigate these risks.
How TokenMinds Accelerates Your EIP-7702 Integration
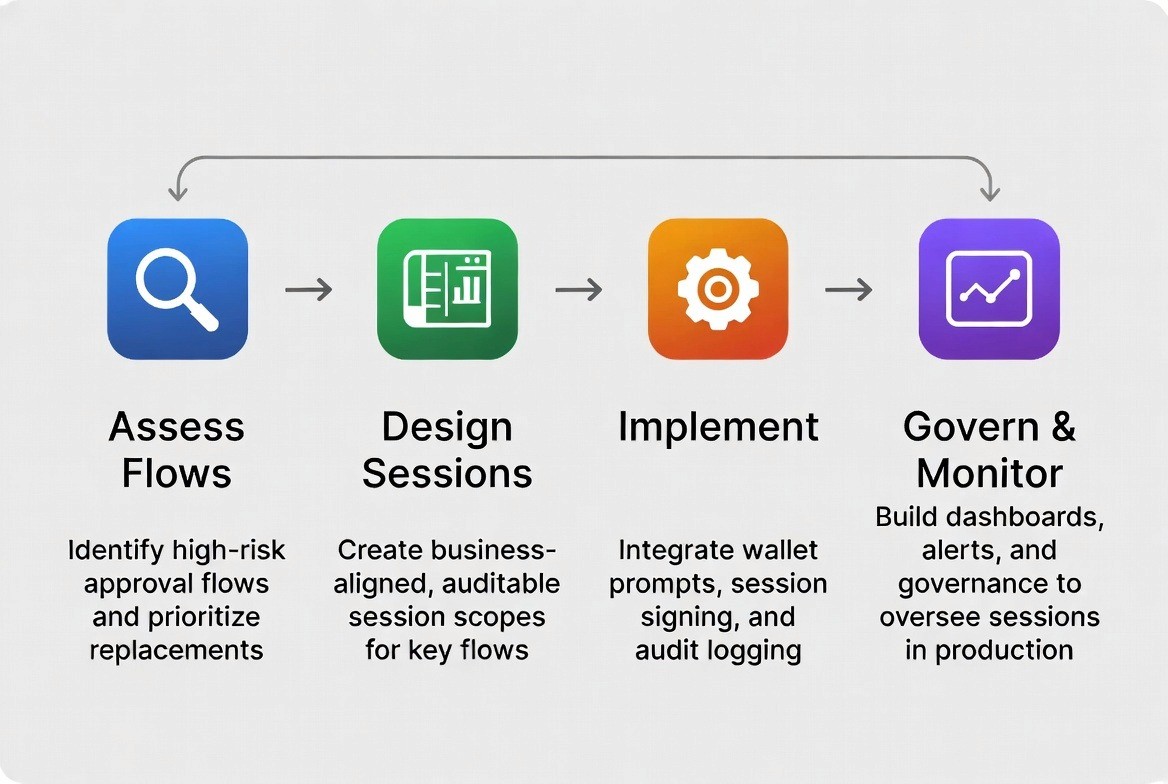
Modern Web3 financial products need safer, smoother transaction flows—but implementing new standards like EIP-7702 can feel complex for internal teams. TokenMinds helps organizations adopt these capabilities with clarity and confidence, ensuring every step is aligned with business goals, user safety, and regulatory expectations.
1. Assess Flows: Identify high-risk approvals and prioritize replacements.
2. Design Sessions: Create business-aligned, auditable session scopes for key flows.
3. Implement: Integrate wallet prompts, session signing, and audit logging.
4. Govern & Monitor: Build dashboards, alerts, and governance to oversee sessions in production.
Conclusion
EIP-7702 represents a fundamental correction to how permissions should work in Web3, not a minor refinement. For companies building financial products on blockchain rails, early adoption offers a meaningful head start—often six to twelve months. Firms that move now will be better positioned to meet institutional expectations as larger pools of capital enter the space and will be ahead of regulators as authorization standards tighten.
Schedule a complimentary consultation with TokenMinds to explore how EIP-7702 can be integrated into your platform’s transaction flows, improving authorization safety and user experience while fitting smoothly into your current systems.








