TL;DR
You’ll learn how to reduce your financial applications' smart contract risk at scale by standardizing code across EVM, WASM, and modern contract languages, replacing one-off audits with automated scanning, risk scoring, and policy-driven approval; turning contract security into a measurable, repeatable control for financial applications.
Financial institutions today face a significant hurdle as they attempt to integrate blockchain technology into their core operations. The primary obstacle is not the speed of the blockchain or the cost of transactions, but rather the way security is managed.
Currently, most financial teams and development groups treat the security of smart contracts as a problem that is solved through audits, as outlined in this guide. An audit is a process where external experts review code line-by-line to identify errors or "bugs" before a product is released. While this process is essential, it is insufficient for securing the global financial system.
The reliance on audits creates a fundamental weakness. Audits are designed to catch mistakes in individual files or specific applications. They are a "point-in-time" check. However, they do not create consistency, predictability, or repeatability across a large portfolio of contracts. When a bank manages thousands of financial agreements, they cannot rely on a system where every agreement is unique and requires a manual, bespoke review.
What is missing from the current landscape is a method to standardize the "execution surface" of smart contracts. The execution surface refers to the parts of the code that actually run and perform tasks. Without a way to standardize this, risk managers cannot measure the risk of a piece of code before it runs. In traditional finance, risk is measured and managed using strict standards.
In the current blockchain environment, this is often impossible. The solution to this problem is a shift in philosophy: moving from "bespoke" (custom-made) code to "standardized" code. This shift transforms smart contract security from a manual audit problem into a measurable risk-engineering problem.
What are Standardized Smart Contracts
It is important to define exactly what is meant by "standardized smart contracts”, as discussed in this reference. These are not just copies of code. They refer to repeatable, proven execution patterns that operate across different runtime layers. These layers include the Ethereum Virtual Machine (EVM), WebAssembly (WASM) environments, and Move-based programming languages.
In a standardized model, developers do not write new, unique code for every deployment. Instead, institutions rely on three key components:
Defined Templates: Pre-written code structures that have been tested and verified.
Constrained Logic: Rules that limit what the code is allowed to do.
Protocol-Level Primitives: Basic building blocks that are built directly into the system.
This approach fundamentally changes when and how security is applied. In the traditional model, security is applied after the code is written, during the inspection phase. In the standardized model, security is applied before the code is even written, during the design phase. This ensures that the risk is managed by design rather than by inspection.
Why Custom Smart Contracts Create Structural Risk
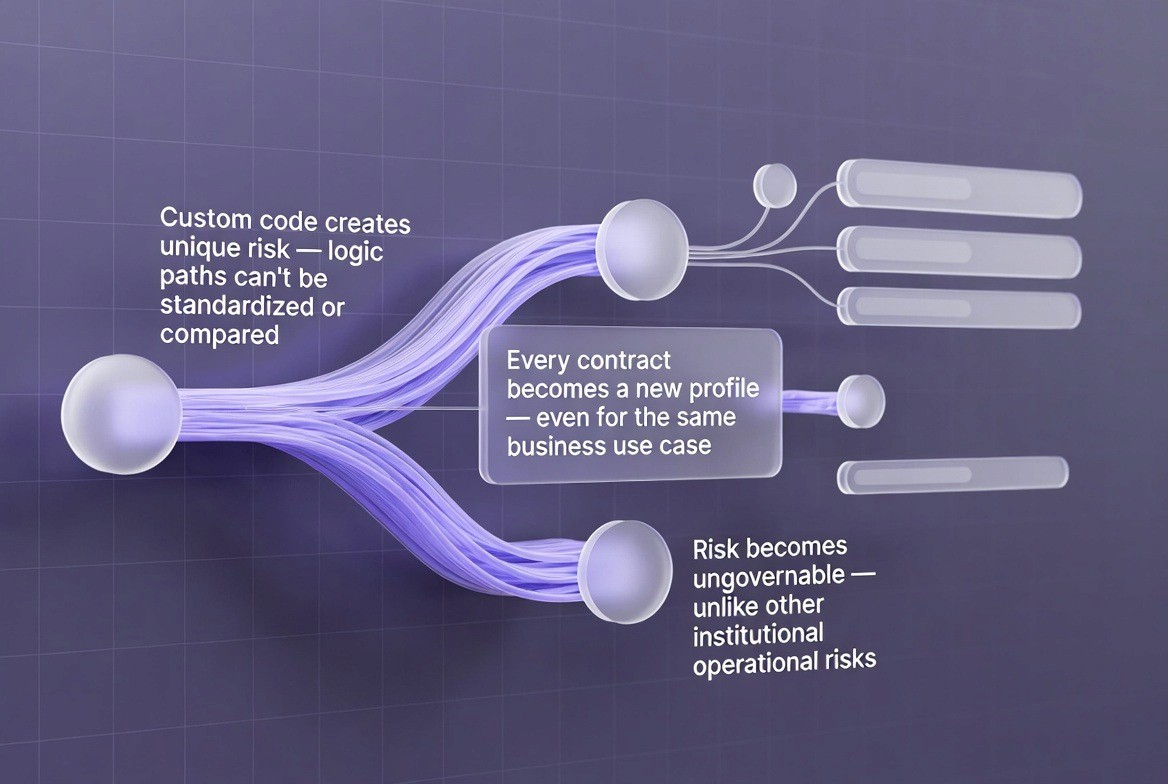
When developers write custom smart contracts for every new application, they introduce what is known as "structural risk." Structural risk refers to dangers that are built into the very design of the system. Custom smart contracts introduce unique "logic paths." A logic path is the specific sequence of decisions and steps a computer program follows to complete a task. Because every custom contract is written differently, these logic paths cannot be easily compared, modeled, or governed.
The Goal of Smart Contract Standardization
Every time a developer creates a new contract, they create a brand new risk profile; For example, if a large financial institution wanted to store their clients’ funds in a digital safe (a “digital vault”) and ten developers wrote ten separate contracts to do exactly that, each would have been written differently and as such each one could expose the company to different types of risk. For instance, one developer may have used a complicated methodology to calculate balance amounts while another may have used a very simple way to do so; similarly, one developer may have allowed for immediate withdrawal from the vault while another required some form of waiting period.
As a result of the complete lack of standardization, the financial institution has no means by which to govern itself. Governance refers to being able to set and enforce rules and standards across an organization. As a result, if the risk management group does not know what type(s) of risks are being created through the development of each smart contract, then they can’t develop policies to mitigate those risks and therefore cannot treat smart contract exposure as an operational risk similar to how it would be treated in traditional finance.
Operational risks in traditional finance are both standardized and managed on a day-to-day basis. In contrast, in the custom blockchain environment, there is no way to manage the risk in order to govern it.
Feature | Custom Smart Contracts | Standardized Smart Contracts |
Logic Paths | Unique, complex, and unpredictable | Fixed, simple, and pre-defined |
Comparability | Impossible to compare across apps | Easily comparable and measurable |
Risk Profile | Creates a new profile for every app | Maintains a consistent profile |
Governance | Difficult to enforce centrally | Automated and policy-driven |
Dependence | Relies on manual code reviews | Relies on pre-approved templates |
The ultimate objective is to change the nature of smart contracts. The goal is to turn them from bespoke software projects into managed financial instruments. A managed financial instrument is a product that behaves predictably and can be regulated, traded, and understood by all parties involved.
How to Standardize Smart Contract Code in Financial Applications
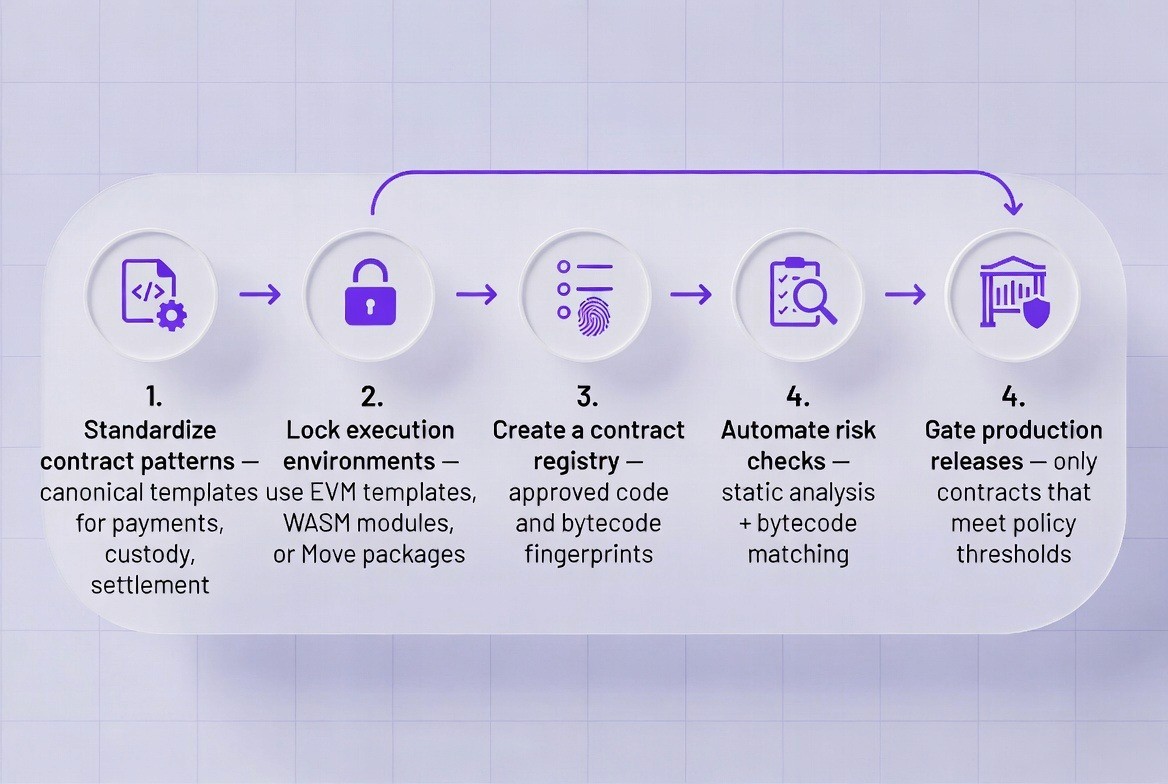
To achieve this transformation, institutions must follow a rigorous, structured process. This is not a vague guideline but a specific set of technical steps. There are five critical steps to standardize smart contract code in financial applications.
1. Define Approved Contract Patterns
Approved contract patterns need to be created through a process called the "creation of canonical templates." Canonical templates are officially approved versions of pieces of code. They must be identified so financial institutions can have a standard way of performing their most frequent actions using the blockchain and a pattern for each action has been created. Some examples of these common actions are:
Payments: The logic behind the transaction transferring value from one party to another.
Custody: The logic associated with holding assets securely and safely in custody.
Tokenization: The act of creating a digital token representing a physical world asset, as explained in this overview.
Settlement: The finality of a trade or the settlement of an agreement.
By defining these patterns, the institution ensures that every time a payment is made, it uses the exact same secure code. There is no variation and no room for creative errors.
2. Lock Execution Environments
Standardization requires control over the environment where the code runs. Institutions cannot allow code to run just anywhere. They must "lock" the execution environment. This means they standardize on specific technical foundations, such as:
EVM Templates: Specific configurations of the Ethereum Virtual Machine.
WASM Modules: Approved modules for WebAssembly.
Move Packages: Verified packages for the Move language.
By locking the environment, the institution limits "execution variance." Variance occurs when code behaves differently because the computer running it is configured differently. Eliminating variance is key to predictability.
3. Build a Contract Registry
An institution needs a central library to track its software. This is called a "Contract Registry." This registry does not just store the source code (the text written by humans); it maintains the "bytecode fingerprints." Bytecode is the machine-readable translation of the code. A fingerprint is a unique digital identifier for that bytecode.
By maintaining a registry of approved bytecode fingerprints, the institution can instantly verify if a contract running on the blockchain is an approved version or an unauthorized modification.
4. Automate Risk Scanning
High-speed finance can't rely on manual review of humans for risk assessment. Therefore, institutions should use an Automated Risk Scanning process. Automated Risk Scanning will involve a software application reviewing contracts prior to them being deployed with two primary functions:
Static Analysis: The application will read through the code as written without executing it to identify obvious logical errors or other potentially hazardous patterns.
Bytecode Matching: The application will compare the compiled code of each contract to the fingerprinted approved versions stored within the Contract Registry.
The Automated Risk Scanning function will ensure that each individual contract is reviewed for compliance to the safety parameters with each and every deployment.
5. Enforce Policy at Release
The final step is enforcement. The system must have "policy-driven deployment gates." A deployment gate is a checkpoint that stops code from going live ("production") unless it passes specific tests.
The system enforces a rule that allows production deployment only for contracts that pass governance checks and meet specific risk thresholds. If a contract is too complex, or if it uses unapproved patterns, the gate remains closed, and the code cannot be launched.
What Changes in the Smart Contract Code When You Standardize
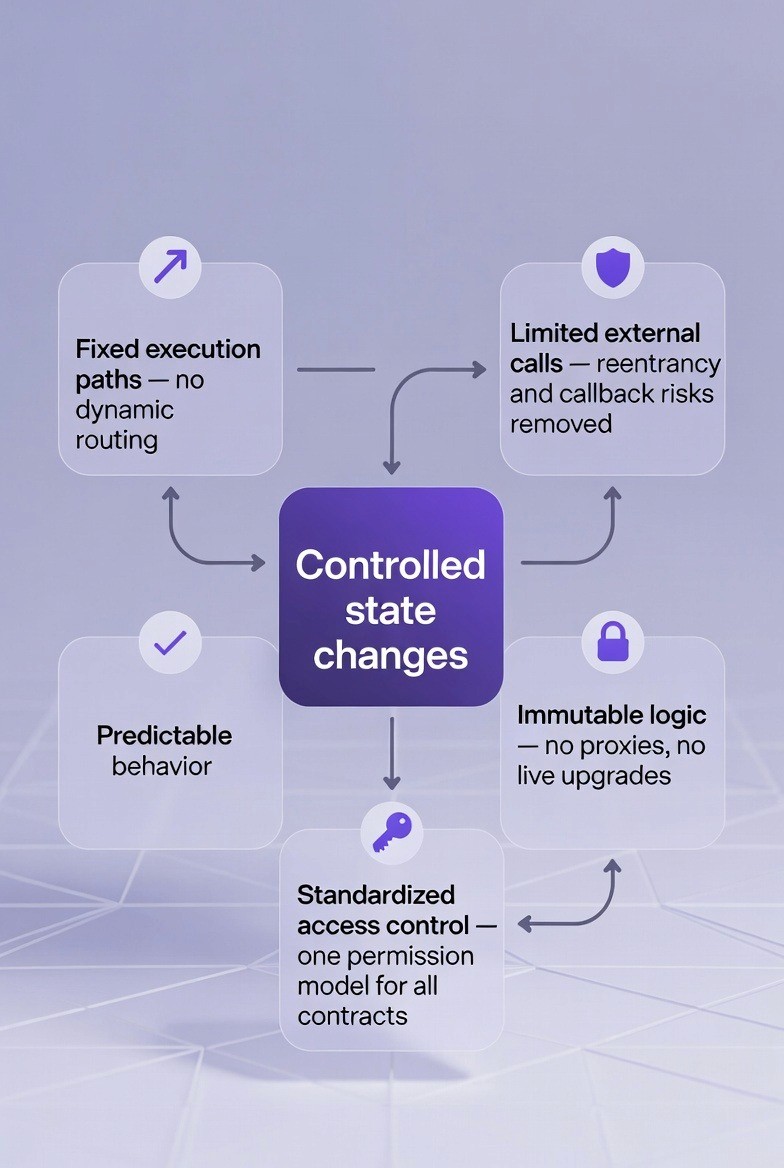
When an institution transitions from custom code to standardized code, the technical structure of the software changes fundamentally. These changes are not just cosmetic; they alter the control flow, state management, and trust boundaries of the application. There are five specific technical changes that occur.
1. Execution Paths Become Fixed
In custom coding, developers often use "arbitrary branching." This means they write complex rules using nested [if/else] statements and "dynamic dispatch" (where the program decides which function to run while it is running). This creates a web of possibilities that is hard to test.
In standardized code, these arbitrary branches are replaced. The code moves to "predefined execution paths." The software functions like a "template-based state machine." A state machine is a system that can only be in one of a few specific conditions (states) and moves between them using strict rules.
Impact: This results in fewer conditional paths. There are fewer places for hidden behaviors to exist and fewer "blind spots" that auditors might miss.
2. State Changes Become Explicit and Constrained
"State" refers to the data stored in the contract, such as user balances or ownership records. In custom code, developers often write "ad-hoc" storage writes. This means any function might change the data in unexpected ways.
In standardized code, data changes are "whitelisted." This means there is a list of allowed changes, and only those changes can happen. These transitions are enforced by "canonical state handlers"; special code modules whose only job is to manage data safely.
Impact: This ensures there is no "ad-hoc state mutation." A mutation is a change. By preventing random changes, the system prevents unexpected side effects where one action accidentally corrupts data elsewhere.
3. External Calls Are Minimized or Removed
Smart contracts often need to talk to other contracts. In custom code, developers use commands like call or delegatecall to interact with external systems. This is flexible but dangerous. It introduces "reentrancy risk." Reentrancy is a hacking technique where a malicious external contract interrupts a process (like a withdrawal) and calls back into the original contract to drain funds before the balance is updated.
In standardized code, these external calls are restricted. Often, the "call surfaces" (the parts of the code that accept outside calls) are strictly limited, or external calls are removed entirely.
Impact: This eliminates reentrancy risk and "callback exploits." If the contract never calls out to an untrusted source, the untrusted source can never attack it back.
4. Upgrade Logic Is Removed from Production Paths
Many custom contracts are built to be upgradeable. Developers use "proxy patterns" or mutable addresses so they can fix bugs later. However, this creates a risk: if the developers can change the code, they can also break it or steal funds (intentionally or accidentally).
In standardized code, the logic is often "immutable." This means the bytecode cannot be changed once it is deployed. If a change is needed, a new version is deployed, and users move to the new version.
Impact: This prevents "behavior drift." Behavior drift happens when a contract acts one way today and a different way tomorrow. With immutable code, governance actions cannot accidentally alter the contract's behavior after deployment.
5. Permission Checks Move to a Single Layer
In custom code, security checks are often scattered. A developer might write require(msg.sender == owner) at the start of every sensitive function. If they forget this line in just one place, the contract is vulnerable.
In standardized code, permission checks are centralized. The system uses a single, audited "access-control module." This module is used across all contracts in the portfolio.
Impact: This guarantees consistent authorization. Every contract uses the exact same lock on the door.
Table of Comparison: Custom and Standardize Approach
Code Aspect | Custom Code Approach | Standardized Code Approach | Security Consequence |
Execution Flow | Complex branching & dynamic choices | Fixed paths & state machines | Fewer bugs, easier to predict |
Data Handling | Random/Ad-hoc updates | Strict, whitelisted transitions | No accidental data corruption |
External Calls | Frequent, open calls | Restricted or removed | No reentrancy attacks |
Upgradability | Proxies allow code changes | Immutable (unchangeable) code | No behavior drift or hidden changes |
Permissions | Checks scattered in files | Centralized access module | Consistent security rules |
Frameworks 1: Standardized EVM Bytecode Templates
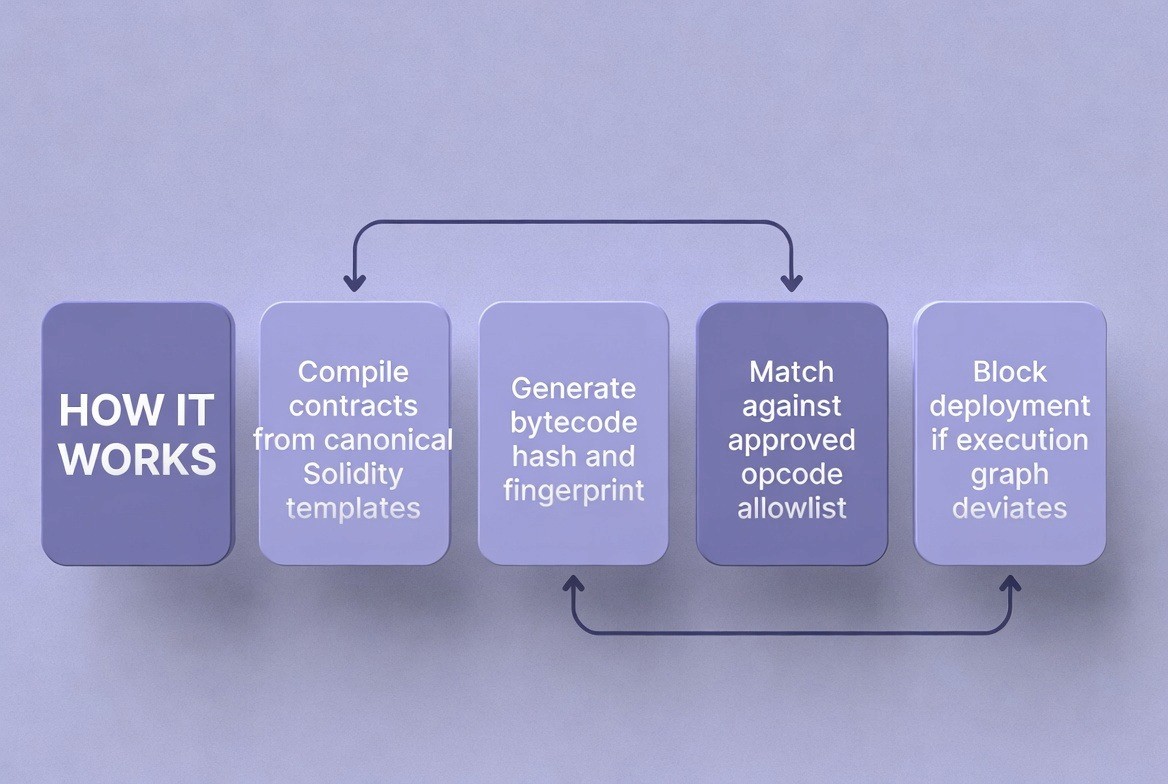
The Ethereum Virtual Machine (EVM) is the most widely used environment for smart contracts. Standardization in the EVM focuses on "bytecode templates."
When institutions standardize EVM usage, they stop reviewing just the source code. Instead, they govern the "bytecode patterns." Bytecode is the low-level instruction set that the computer executes. By focusing on bytecode, the institution removes the risk that the compiler (the tool that turns source code into bytecode) made a mistake or that the source code was misleading.
Key Features of EVM Standardization:
Repeatable Execution Logic: The code performs the exact same steps every time it is run.
Predictable Gas Paths: "Gas" is the fee paid to run a transaction. Standardized code has predictable costs, which is vital for financial planning.
Reduced Hidden Behavior: Because the bytecode is matched against a known template, there is no room for hidden malicious features.
The Workflow:
Compile: Developers compile their contracts from Solidity (source code) into bytecode.
Match: The system generates a hash (fingerprint) of the bytecode and an "opcode graph" (a map of the instructions). It compares these against the approved templates in the allowlist.
Decision: If the execution logic deviates even slightly from the template, the system blocks the deployment. If it matches, it allows it.
Frameworks 2: WASM-Based Contract Modules
WebAssembly (WASM) is a newer technology that allows code to run in a very controlled environment. It is becoming popular for financial applications because it offers strong boundaries.
WASM allows contracts to run in "constrained, sandboxed runtimes." A sandbox is a safety mechanism that isolates a program so it cannot access data or parts of the system it is not supposed to touch. This limits unexpected behavior compared to the EVM, which is sometimes more open.
Key Features of WASM Standardization:
Bounded Execution Environment: The code runs in a tight container with strict rules.
Deterministic Runtime Behavior: The output of the code is mathematically determined and will never vary based on randomness.
Easier Formal Verification: "Formal verification" is a mathematical method of proving code is correct. WASM's structure makes this process easier.
The Workflow:
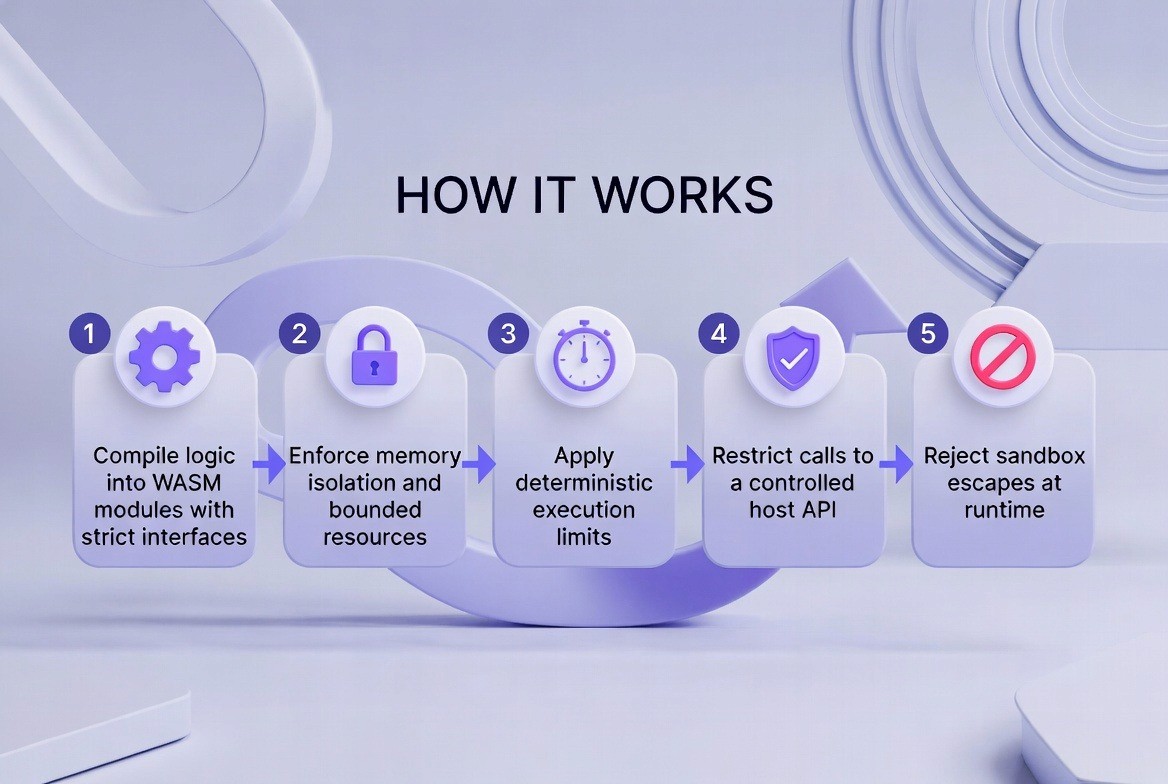
Compile Logic: Logic is compiled into WASM modules with strict "interfaces" (connections).
Enforce Isolation: The system enforces memory isolation, ensuring the module cannot read other memory.
Apply Limits: The system applies deterministic limits on execution resources (like CPU time).
Restrict Calls: The module is restricted to calling only a controlled "host API."
Reject Escapes: The runtime automatically rejects any attempt by the code to escape the sandbox.
Frameworks 3: Move-Based Languages for Financial Logic
Move is a programming language specifically designed for finance. It introduces the concept of "resource-oriented programming." In most languages, a digital token is just a number in a database variable. In Move, a token is a "resource"—a digital object that follows physical laws.
This alignment with financial assets reduces entire classes of bugs that are common in traditional smart contracts.
Key Features of Move Standardization:
No Accidental Destruction: Assets cannot be "dropped" (deleted) accidentally. The language forces the developer to handle the asset safely.
No Duplication: Assets cannot be copied. You cannot take one coin and copy it to make two.
Strong Type and Ownership Guarantees: The language enforces strict rules about who owns an asset and where it can go.
Built-in Safety: Safety logic for tokens is built into the language itself.
The Workflow:
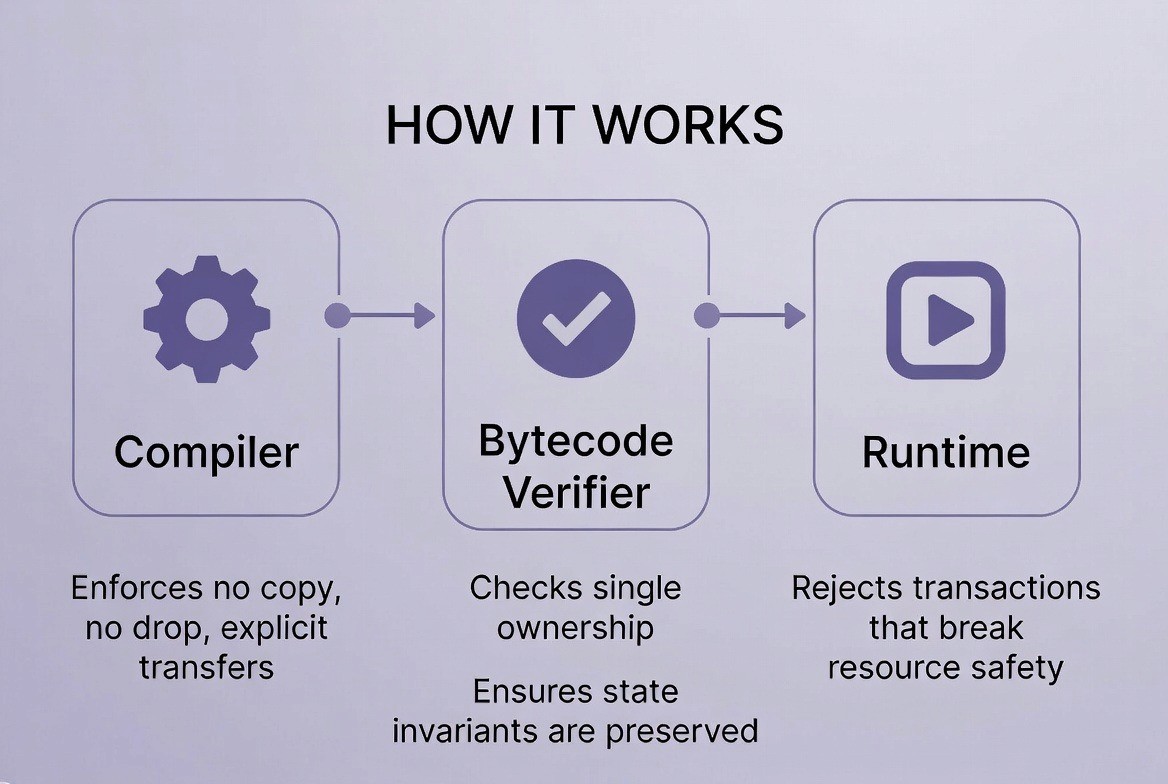
Compiler: The compiler enforces rules like "no copy," "no drop," and "explicit transfers." If a developer tries to break these rules, the code will not even compile.
Bytecode Verifier: Before the code runs on the blockchain, a verifier checks for single ownership. It ensures that "state invariants" (rules that must always remain true) are preserved.
Runtime: The runtime rejects any transaction that attempts to break resource safety.
Other Solution: Protocol-Level Enforcement
In some cases, the most effective way to reduce risk is to remove the smart contract entirely. This is called "Protocol-Level Enforcement."
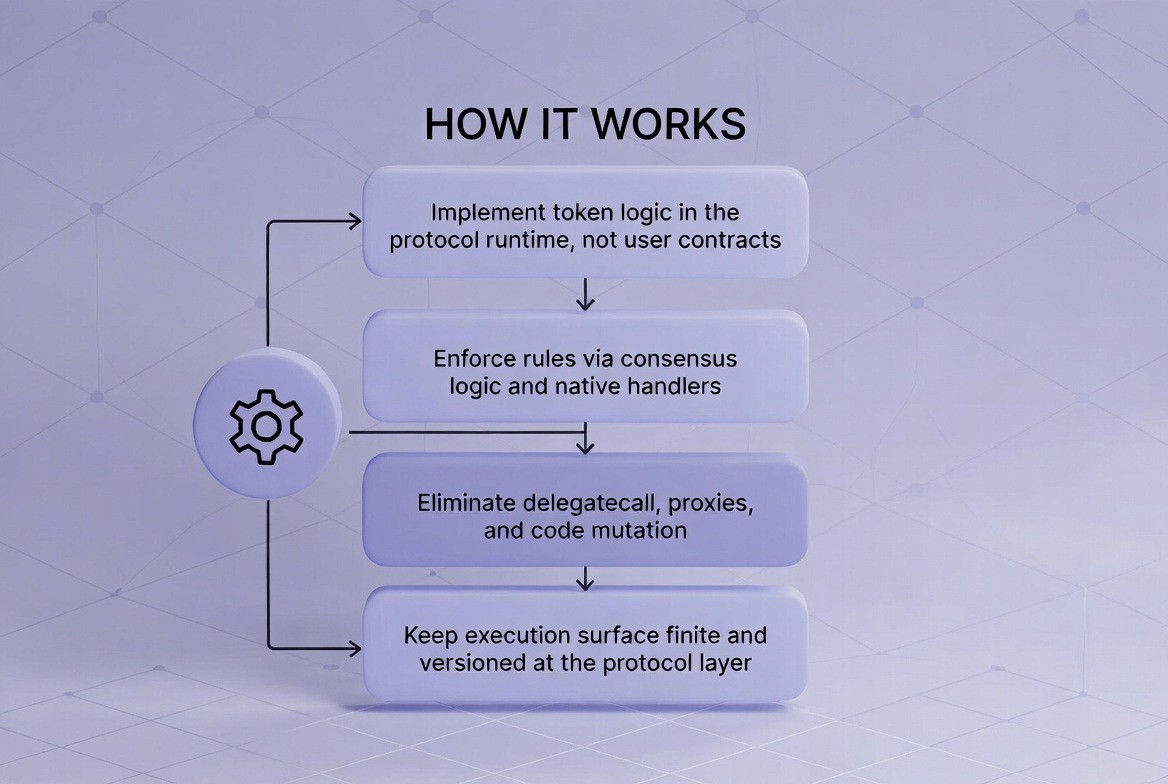
Instead of writing custom logic for tokens or assets in a user-deployed contract, the logic is implemented directly in the "protocol runtime." This means the rules of finance are baked into the blockchain network itself.
Key Features:
Network-Enforced Rules: The rules are enforced by the consensus of the entire network, not just one file.
No Upgradeable Proxies: There are no admin keys or proxies that can be hacked to change the rules.
Fixed Execution Surface: The options available to users are finite and known.
How It Works:
Token logic is implemented in the protocol runtime. The network uses "native handlers" to process transfers and logic. This eliminates the need for delegatecall, proxies, and code mutation. The execution surface is versioned at the protocol layer, meaning it only changes when the entire network agrees to an upgrade.
Turning Contract Security Into a Measurable Control
The ultimate benefit of standardization is that it turns security into a number. It transforms a qualitative assessment ("This code looks okay") into a quantitative control ("This code has a risk score of 12").
How This Works Technically
1. Automated Static Scanning
The process begins with automated scanning. Contracts are analyzed at the bytecode level and the "AST" (Abstract Syntax Tree) level. The AST represents the logical structure of the code. The scanner compares this structure against the approved execution patterns.
2. Deterministic Risk Scoring
The system assigns a risk score to every contract. This score is not a guess; it is calculated based on specific factors:
Call Graph Complexity: How complex is the flow of the program? More complexity equals a higher score.
Permission Surface: How many people have administrative powers? More admins equals a higher score.
Upgradeability: Can the code be changed? Upgradeable code gets a higher risk score.
3. Policy-Driven Deployment Gates
This score drives the deployment process. The CI/CD (Continuous Integration/Continuous Deployment) pipeline is the system that moves code from development to production. It is configured with "deployment gates." If a contract's risk score is below the allowed threshold, the gate opens. If the score is too high, the CI/CD pipeline blocks the deployment automatically.
4. Continuous Re-evaluation
Risk is dynamic. A contract that is safe today might be risky tomorrow if a new vulnerability is discovered. Therefore, the system performs "continuous re-evaluation." Contracts are rescored regularly as standards change, compilers are updated, and threat models evolve.
Real Use Cases of Standardized Smart Contract in Finance
Standardization is not a theoretical concept; it is already being used by major protocols in the Decentralized Finance (DeFi) sector to manage billions of dollars.
Aave: Standardized Yield Vaults
Aave, a leading lending protocol, implemented "ERC-4626" compliant yield vaults to serve institutional capital. ERC-4626 is a standard for tokenized vaults.
Standardized Interface: Aave uses standard functions like
deposit(),withdraw(),mint(), andredeem(). It also uses view functions likeconvertToAssets()andpreviewDeposit().Benefits:
Off-chain Risk Aggregation: Because the API (Application Programming Interface) is the same for all vaults, external risk systems can monitor all of them easily.
Multi-protocol Composability: The "vault shares" (tokens representing the deposit) can be used easily in other DeFi applications.
Automated Compliance: A "StaticATokenFactory" registry ensures there is only one vault per asset. This prevents fragmentation and confusion about who the counterparty is.
Efficiency: It uses standardized gas-less approvals (EIP-2612). This allows for single-transaction workflows, which are much better for institutional operations than the old multi-step process.
Yearn Finance
Yearn Finance is a protocol that automates yield generation. It evolved from a "monolithic" model (where every vault was a unique, massive file) to a standardized "multi-strategy framework."
ERC-4626 Compliance: All vaults follow the standard interface, enabling integration with risk monitoring engines.
Strategy Template System: This is the core of their standardization. Developers do not write strategies from scratch. They use a "Base Strategy" contract and only override three specific functions to create a new strategy.
Benefits: The base strategy is audited once and reused many times. This drastically reduces the surface area for bugs.
RoleManagerFactory: They use a factory to automatically configure access control. It assigns roles like governance, management, and debt allocators automatically.
Standardized Accounting: Fee accounting is handled by pluggable "Accountant" contracts. Debt rebalancing across multiple strategies is handled by a standardized "DebtAllocator."
The Outlook
The future of smart contract security is clear. The responsibility for risk is moving from the individual developer to the institutional governance team.
In the coming years, standardized execution environments will replace bespoke code as the default for financial use cases. Bespoke code will fade away in finance because the risks are simply too high to manage. Security teams will no longer be tasked with reviewing individual contracts one by one. Instead, they will manage "contract portfolios"—large groups of contracts that all follow the same strict standards.
FAQ
How to standardize smart contract execution for financial applications
Standardization begins by fixing the execution surface rather than reviewing individual implementations. Financial institutions define canonical contract templates for common functions such as payments, custody, settlement, and tokenization, then restrict deployment to those templates only. By locking execution environments like EVM bytecode profiles, WASM modules, or Move packages, institutions eliminate behavioral variance and ensure every contract executes within a known and governed runtime model.
What actually changes when smart contract code is standardized?
Standardization constrains execution itself by replacing arbitrary branching and dynamic dispatch with fixed templates, deterministic state machines, and whitelisted state transitions. This reduces cyclomatic complexity, eliminates hidden side effects, and makes contract behavior predictable before deployment, turning security from inspection into classification.
How does this reduce real-world exploit risk?
By design, standardized execution removes entire attack classes: reentrancy disappears when external calls are minimized, upgrade exploits vanish when immutable bytecode replaces proxy patterns, and permission failures shrink when access control is centralized into audited modules. Instead of chasing vulnerabilities after deployment, institutions eliminate the structural conditions that allow them to exist.
How does standardized code turn security into a measurable control?
Once execution is standardized, contracts can be fingerprinted at the bytecode level and matched against approved templates, then scored using deterministic metrics like call-graph complexity, mutability, and administrative surface area. These scores feed directly into CI/CD deployment gates, so contracts are approved or blocked by policy thresholds rather than subjective review.
Why does this approach work across different blockchain stacks?
Modern runtimes embed safety at the execution layer: EVM bytecode templates lock opcode graphs and gas paths, WASM enforces sandboxed and deterministic execution, and Move guarantees asset safety through resource-based semantics. Together, they answer the institutional challenge of transforming smart contracts from bespoke software into governed financial instruments by making risk engineered into the system rather than audited after deployment.
How TokenMinds Supports Standardized Smart Contract Implementation

TokenMinds is dedicated to helping financial institutions navigate this transition. The firm assists institutions in designing smart-contract architectures that are based on standardization principles.
TokenMinds supports teams in three critical areas:
Selection: Helping teams select the right execution environments (EVM, WASM, or Move).
Definition: Helping teams define approved contract patterns and templates.
Automation: Helping teams embed automated risk controls into their deployment pipelines.
By adopting these services, institutions can scale their blockchain adoption with confidence. They can ensure that their contract risk remains measurable, governable, and auditable, transforming blockchain from a risky experiment into a reliable financial infrastructure.
Conclusion
Standardizing smart contract code changes how financial institutions handle blockchain risk. Instead of relying on one-off audits and custom solutions, standardization makes security repeatable and measurable. By fixing execution environments, using approved templates, and enforcing policy-driven deployment, institutions can eliminate structural risk at its source. This leads to a shift from reactive security to engineered risk management. Smart contracts start to act less like experimental software and more like regulated financial instruments. They can scale safely across payments, custody, settlement, and tokenization.
If your company is looking into blockchain for financial applications and wants to reduce operational, security, and compliance risks, now is the time to move beyond custom code.Schedule a free consultation with TokenMinds to see how standardized smart contract frameworks can help your organization create safer architectures, automate risk controls, and make smart contract security a predictable, auditable process.








