TL;DR
This article explains how to identify whether your business is limited by transaction scale and cost or by data privacy and regulatory exposure. It will show how to send public, high-volume flows to zkSync and how to send sensitive, regulated flows to Midnight. Business leaders will learn the technical differences between these platforms and understand which platform serves each organizational need.
The Fundamental Choice: Scale Versus Privacy
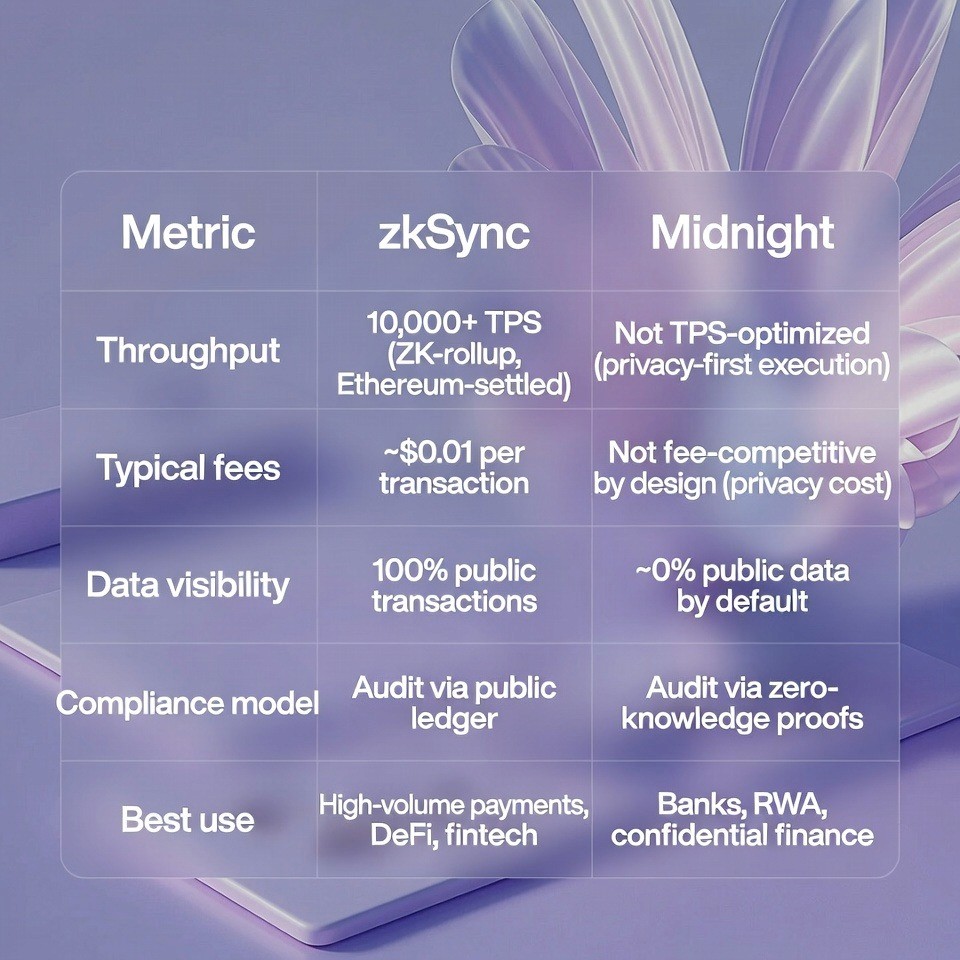
At an institutional level, zkSync and Midnight solve different core constraints. These platforms represent two different approaches to blockchain design, as outlined in this overview. Neither platform is better than the other. Each platform is better for different types of organizations and different types of transactions.
zkSync: The Scale-Focused Platform
zkSync (Era) is an Ethereum Layer-2 zero-knowledge rollup platform. A Layer-2 platform means that it builds on top of Ethereum, not as a separate blockchain. A zero-knowledge rollup is a technical design that processes transactions off the main network and then proves that those transactions are correct to Ethereum, using verification approaches discussed here. This design allows zkSync to scale to high transaction volumes.
zkSync is designed to scale existing Ethereum finance. It is optimized for public, high-volume execution. This means that zkSync is built for organizations that need to process many transactions, need those transactions to be public and transparent, and need to do this without high costs.
Performance Metrics of zkSync
zkSync achieves throughput of ten thousand or more transactions per second. Throughput means the number of transactions the network can process in one second. Ethereum, the main blockchain, processes approximately fifteen to thirty transactions per second. zkSync processes more than three hundred times more transactions than Ethereum.
Typical transaction fees on zkSync cost approximately one cent per transaction. On Ethereum during periods of high congestion, transaction fees can cost multiple dollars per transaction. This one cent fee on zkSync makes it economically practical for organizations to process high volumes of low-value transactions.
The zero-knowledge rollup design works through batching. zkSync collects thousands of transactions together. It creates a zero-knowledge proof that proves all of those transactions are correct. It submits only that proof to Ethereum, not the individual transactions. This batching reduces the amount of data that must be stored on Ethereum and therefore reduces the cost per transaction.
zkSync inherits all of Ethereum's security properties. Ethereum is the most secure blockchain in operation. It uses a proof-of-stake consensus mechanism that requires validators to hold significant amounts of Ethereum to validate transactions. If validators act dishonestly, they lose their money. This economic incentive creates strong security. Because zkSync submits its proofs to Ethereum, zkSync transactions receive the same level of security as Ethereum transactions.
Data Visibility on zkSync
Data visibility on zkSync shows one hundred percent public transactions. Every transaction on zkSync is completely transparent. All transaction details are publicly visible on the blockchain. While identity information must be handled off-chain (no personal data ever touches the blockchain itself), the transaction history itself is fully auditable and transparent. Anyone can observe the transaction history.
The compliance model relies on audit via public ledger. This means that when an auditor or government agency needs to check whether transactions are correct, they can look at the public transaction record. The public record shows every transaction. Auditors can verify that transactions follow all rules by examining this public record.
Best Uses of zkSync
zkSync is best used for high-volume payments, decentralized finance applications, and fintech platforms. Decentralized finance means financial services that are offered on blockchain networks without traditional banks. Fintech means financial technology companies that offer financial services through technology rather than through physical locations.
Midnight: The Privacy-Focused Platform
Midnight is a privacy-first Layer-1 blockchain built as a Cardano partner chain. A Layer-1 blockchain is a separate blockchain, not built on top of another blockchain. Midnight is designed to work with Cardano, another blockchain, and to benefit from Cardano's security and technology, as discussed in this reference.
Midnight is designed for confidential computation. Confidential computation means that the blockchain performs calculations and validations without revealing the information used in those calculations. Midnight is optimized for regulated and sensitive data flows. This means that Midnight is built for organizations that need to process transactions while keeping sensitive information private.
Performance Metrics of Midnight
Midnight's throughput is not optimized for maximum transactions per second. Because Midnight focuses on privacy, it uses more computational resources per transaction than a public blockchain would use. This means that Midnight can process fewer transactions per second than zkSync. Midnight is not suitable for applications that need to process millions of transactions per second.
Typical fees on Midnight are not fee-competitive by design. The privacy protection that Midnight provides requires additional computational work. This additional work increases the cost per transaction. Organizations that choose Midnight accept higher fees in exchange for privacy protection.
Data Visibility on Midnight
By default, there is essentially no public data available for users to view on Midnight (i.e., around zero percent). Unlike many other blockchains which store raw user data (e.g., transaction info & user identities), Midnight will only store "mathematical proof" that verifies the validity of a transaction. If a regulator or auditor wants to see certain data, the Data Holder can selectively disclose that data to those entities while keeping the remainder of the transaction history hidden from those individuals/entities.
Midnight’s compliance model relies upon auditing via zero-knowledge proofs. In essence, if an auditor or a government entity wishes to determine if a transaction was done correctly, they will review mathematical “proofs” demonstrating that the transaction occurred properly – however the actual transaction details are never revealed. An organization may be able to demonstrate that they have complied with applicable laws/rules, etc. but will be unable to provide details regarding their individual customer transactions as well as internal operational activities.
Best Uses of Midnight
Midnight is primarily intended for use in banking systems, real-world asset platforms and confidential finance. Real-world asset platforms are companies which convert legal documents or physical property into digital tokens and store them on a blockchain. Confidential finance relates to the provision of financial services where there are confidentiality obligations (e.g., bank customer data).
The Decision Matrix: zkSync vs Midnight
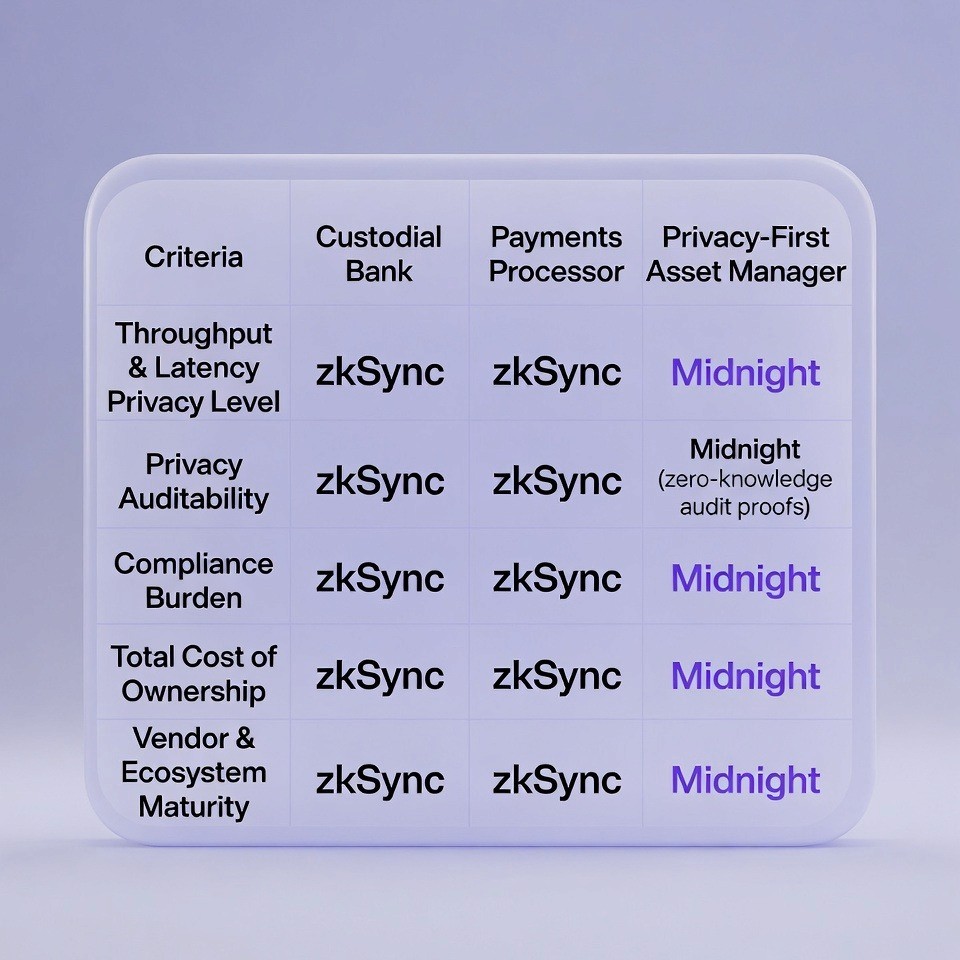
Institutions evaluate platforms across weighted business criteria, not just technical features. The decision matrix below shows how different types of organizations should evaluate each platform based on their specific needs.
ZkSync is suitable for companies with a high volume of transactions, such as gaming platforms, exchanges, decentralized finance (DeFi) projects, consumer-facing fintech companies, etc., as these types of companies require a high volume of transactions per second (throughput), which must confirm rapidly (low latency), while also keeping transaction costs extremely low (fees). The company's public nature, through auditability, requires transparency in how each transaction was executed, so that all stakeholders know exactly what happened at the time it happened. ZkSync provides the necessary tools to enable the rapid execution of large scale settlements, as well as, real-time financial transactions.
Midnight is suitable for regulated financial institutions, asset tokenization companies, and enterprise network companies who need to comply with regulatory requirements. These types of companies have different needs than those using zkSync. For example, regulated financial institutions require confidentiality in their transactions, and the ability to selectively disclose certain information to certain parties without disclosing all of the information. Midnight provides the tools for companies to provide "zero knowledge" audit proofs, enabling regulated financial institutions to demonstrate compliance with regulations without revealing sensitive financial or client information.
Decision Matrix: Organization Type and Platform Suitability
Organization Type | Throughput & Latency Needs | Privacy Level | Auditability Requirements | Compliance Burden | Total Cost of Ownership | Vendor & Ecosystem Maturity |
Custodial Bank (Bank Holding Customer Funds) | zkSync (for settlement speed) | Midnight (data privacy) | zkSync with zero-knowledge proofs (hybrid approach) | Midnight (privacy protection) | zkSync (lower cost) | zkSync (mature) |
Payments Processor (Company Processing Payments) | zkSync (high throughput) | zkSync (transactions already public) | zkSync (transparent records) | zkSync (simpler compliance) | zkSync (low fees) | zkSync (mature) |
Asset Manager (Organization Managing Investments) | zkSync (settlement speed) | Midnight (portfolio privacy) | Midnight (selective disclosure) | Midnight (regulatory protection) | Midnight (higher cost acceptable) | zkSync (existing Ethereum skills) |
Privacy-First Financial Institution | Midnight (acceptable throughput) | Midnight (core requirement) | Midnight (privacy-first audits) | Midnight (integrated approach) | Midnight (accept higher costs) | Midnight (specialized tools) |
In order to fully understand the reasoning behind this choice, it is important for you to consider how to map your organizations' needs with regard to six factors including: the amount of required throughput and latency, how much private transactions are required, what type of auditing (i.e., full transparent versus zero knowledge) will be used, the regulatory balance that exists between privacy and reporting requirements, the total cost of owning a system based on transaction fees and the ability of your teams to implement the solution as it relates to the vendors available tools and ecosystems.
The Compliance Model: zkSync vs Midnight

Why Compliance Model Matters
The fundamental principle is that blockchain architecture must align with transparency needs or privacy obligations. Different organizations have different legal requirements. Some organizations must show all transaction details to regulators. Other organizations must hide transaction details from the public and from competitors while showing selective information to regulators. Choosing the wrong compliance model creates regulatory risk and increases compliance costs.
zkSync Compliance Approach
For zkSync, identity and Know-Your-Customer data are handled off-chain. Know-Your-Customer, abbreviated as KYC, means the process of verifying that a person or organization is who they claim to be. This verification happens in the organization's normal systems, not on the blockchain. The organization completes identity verification before allowing the person to use the blockchain application.
All on-chain transactions remain publicly visible. After a person completes identity verification, their transactions on zkSync are completely transparent. Anyone can see every transaction that person makes. However, the organization maintains the identity information separately. The organization keeps a list connecting each blockchain address to a real person, but that connection remains secret. This connection is never posted to the blockchain.
This approach makes audits and investigations straightforward. Any auditor or government agency can look at the full transaction history. The auditor can verify that transactions follow all rules by examining the public transaction record. However, it requires strict controls to prevent personal data from touching the chain. If personal information ever reaches the blockchain, it becomes permanently visible to everyone.
zkSync and Know-Your-Customer Compliance
Identity data is handled off-chain. This means the organization verifies that a person is who they claim to be before that person uses the blockchain. On-chain activity is fully transparent. Every transaction is visible. The organization must ensure that no personal identification is connected to the blockchain address in any permanent or public way.
zkSync and General Data Protection Regulation Compliance
The General Data Protection Regulation, or GDPR, is a European Union law that protects personal information. GDPR requires organizations to keep personal information private and to delete personal information when people request deletion.
Personal data must never touch the chain. The organization must ensure that no name, address, government identification number, phone number, email address, or any other personal information ever appears on the blockchain. The organization uses off-chain systems to store and manage personal information. The blockchain stores only transaction records and cryptographic addresses, not personal information.
If a person requests that their personal data be deleted, the organization can delete the personal information from its systems. The transaction history remains on the blockchain because the blockchain contains no personal information to delete. This allows the organization to comply with deletion requests while maintaining a permanent transaction record.
zkSync and Subpoena Compliance
A subpoena is a legal order from a court or government agency requiring a person or organization to provide information.
Transaction histories are public and inspectable. When government agencies request information through a subpoena, auditors can simply look at the public record and see every transaction the person made. The organization can provide the government agency with access to this public record. The organization can also provide the government agency with the off-chain identity information connecting blockchain addresses to real people.
This approach makes responding to subpoenas straightforward. The organization does not need to search through private databases. The information is publicly available on the blockchain.
Midnight Compliance Approach
How Midnight Handles Identity and Know-Your-Customer
For Midnight, transaction and identity data are private by default. The person's identity is not visible on the blockchain. Zero-knowledge proofs are used to verify compliance. A zero-knowledge proof is a mathematical certificate that proves something is correct without revealing the underlying information.
Selective disclosure allows regulators to access required information without exposing unrelated data. If a government agency needs to verify that a person passed identity checks, Midnight can show that verification without revealing the person's identity.
Midnight and Know-Your-Customer Compliance
Identity proofs are validated without exposing raw personal data. The blockchain verifies that the person passed identity checks without showing who they are. An auditor can see that a transaction was made by someone who passed identity verification, but the auditor cannot see the person's name or identification number.
Midnight and General Data Protection Regulation Compliance
Data remains user-controlled. The person who made the transaction controls their personal information. Proofs persist without raw data. The blockchain keeps mathematical proofs that the person's transactions were valid, but the blockchain does not keep personal information.
If a person requests that their personal data be deleted, the organization can delete the personal information from its systems. The blockchain still keeps the mathematical proofs that verify the person's transactions were valid. This is permitted under GDPR because the blockchain contains no personal information to delete.
Midnight and Subpoena Compliance
Selective disclosure enables lawful access without full exposure. When a government agency requests information through a subpoena, the organization can show only the information that the government agency needs to see. The organization does not need to expose the person's entire transaction history or business secrets.
For example, a government agency might request information about a specific transaction. The organization can use selective disclosure to show information about that specific transaction without showing other transactions or the person's overall business activity.
The Technical Architecture
Scaling to Millions of Transactions Per Month with zkSync

zkSync enables massive transaction scaling through a Layer-2 zero-knowledge rollup that batches thousands of transactions off-chain. Off-chain means these transactions are not processed on the main Ethereum network. Compressing them into cryptographic proofs known as SNARKs, which are submitted to Ethereum for final verification.
SNARK stands for Succinct Non-Interactive Argument of Knowledge. A SNARK is a type of zero-knowledge proof that is small in size and can be verified quickly. zkSync uses SNARKs to prove that thousands of transactions are correct using a small amount of data.
Step 1: Move Execution to zkSync Layer 2
Route payment and settlement transactions to zkSync to leverage zero-knowledge rollup batching. Rather than processing each transaction on Ethereum's main network, route transactions to zkSync's network. Dramatic increases in throughput are achieved because zkSync processes many more transactions per second than Ethereum.
Inherit Ethereum security when using zkSync. Although transactions are processed on zkSync, the security of those transactions comes from Ethereum. zkSync submits proofs to Ethereum, and Ethereum verifies those proofs. This means that users' funds are protected by Ethereum's security properties.
Step 2: Batch Transactions for Zero-Knowledge Proofs
Aggregate thousands of transfers into single zero-knowledge proofs. When zkSync collects transactions, it does not submit each transaction separately to Ethereum. It bundles many transactions together and creates one proof that covers all of them.
Reduce per-transaction cost through batching. The cost of submitting a proof to Ethereum is split across all the transactions in the batch. For example, if submitting a proof costs one thousand dollars, and the proof covers one thousand transactions, then each transaction costs one dollar. If the proof covers ten thousand transactions, then each transaction costs ten cents. zkSync achieves per-transaction costs of approximately one cent through large batch sizes.
Enable linear scaling without congestion spikes. Traditional blockchains experience congestion when transaction volume increases. Fees rise and confirmation times increase. zkSync avoids this problem. As transaction volume increases, zkSync simply creates more batches. Each batch is processed independently, so increasing transaction volume does not cause congestion.
Step 3: Use Account Abstraction and Paymasters
Enable account abstraction to sponsor gas or fees. Gas is the cost of executing transactions on a blockchain. Normally, the person making a transaction pays the gas fee. Account abstraction removes this requirement. An application can create a special contract called a paymaster that pays gas fees on behalf of users.
Remove user friction when using account abstraction. Normally, blockchain users must acquire and hold the network's native token to pay fees. For example, users must acquire Ethereum to pay fees on Ethereum. This creates friction because users must understand cryptocurrency, acquire it, and manage it. Account abstraction eliminates this friction. Users do not need to acquire or hold any cryptocurrency. The application pays fees automatically.
Simplify high-frequency enterprise flows. Enterprises often need to make many small transactions. If each transaction requires a user to approve the transaction and manage fees, the process becomes inefficient. Account abstraction simplifies this process. Users approve high-level business logic, and the application handles all transaction details and fee management automatically.
Step 4: Separate Execution from Final Settlement
Execute at high speed on zkSync while periodically settling proofs to Ethereum Layer-1. Users receive confirmation almost immediately on zkSync. When a user submits a transaction, the transaction executes on zkSync within seconds. The user receives confirmation that the transaction is complete.
Balance performance and finality guarantees. Although the transaction executes immediately on zkSync, the transaction is not finally settled on Ethereum for several minutes or hours. zkSync batches transactions together and periodically submits proofs to Ethereum. When Ethereum confirms the proof, the transaction is finally settled.
This timing separation is important for some applications. If an application requires absolute cryptographic finality on Ethereum, it must wait for Ethereum confirmation. However, for most applications, the immediate execution on zkSync is sufficient.
Step 5: Integrate Automated Reconciliation
Stream zkSync transaction data into treasury, reporting, and Enterprise Resource Planning systems. Rather than manual reconciliation, transactions flow automatically from zkSync into the organization's accounting systems. Enterprise Resource Planning, abbreviated as ERP, is the system that organizations use to manage their operations and finances.
Support real-time monitoring at million-transaction scale. Treasury teams can monitor settlement positions updating in real-time as transactions execute globally. Rather than waiting days to reconcile transactions, treasury teams can see settlements occurring in real-time.
Reduce manual work through automation. When transactions are reconciled manually, accountants must spend time reviewing transactions and entering them into accounting systems. Automated reconciliation eliminates this manual work. Transactions are entered automatically.
Reduce Data Exposure and Regulatory Risk by 30-50% by Isolating Sensitive Workflows with Midnight
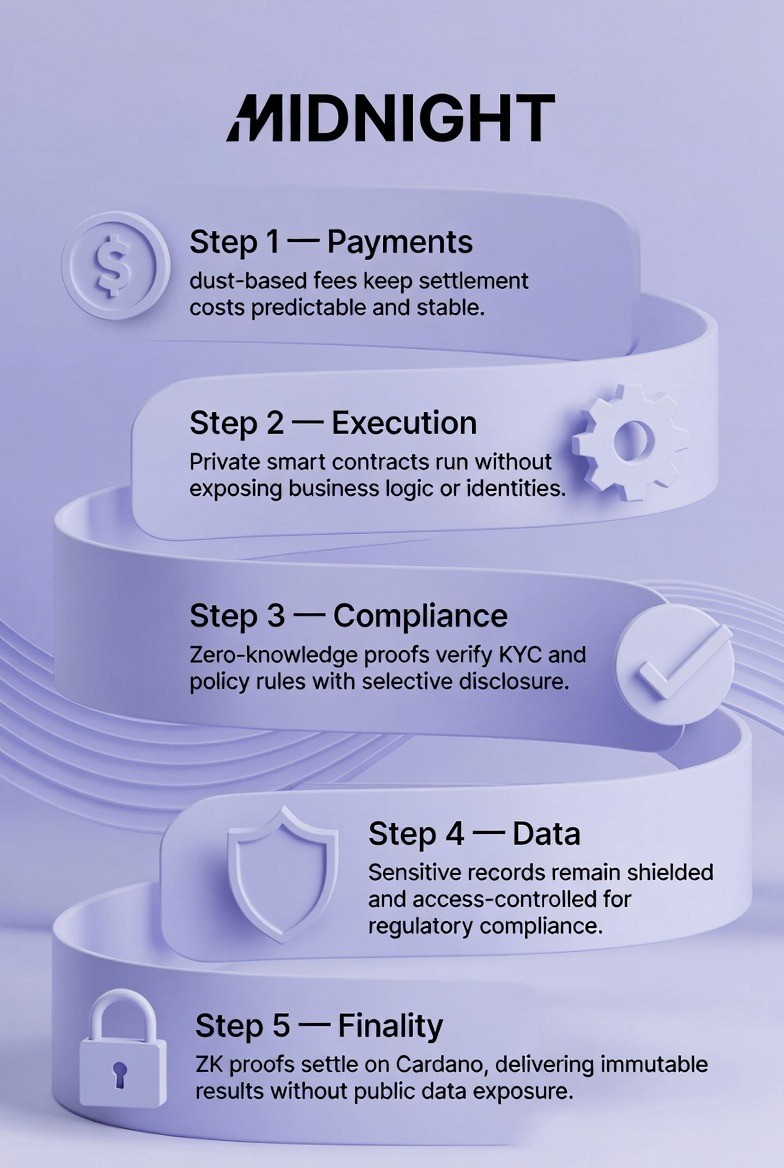
Reducing data exposure and regulatory risk by 30-50 percent involves deploying sensitive workflows on Midnight's Layer-1 blockchain with its dual-state ledger architecture. A dual-state ledger means that Midnight maintains two types of information. Public information and private information are stored separately. Zero-knowledge proofs shield personal information, financial details, and trade secrets from on-chain visibility while enabling transaction validation.
Step 1: Separate Public and Private Data
Design applications so sensitive data stays private by default while transactions are still validated on-chain using zero-knowledge proofs. Identify which information must be visible on the blockchain and which information must remain private. Sensitive information that should remain private includes personal names, identification numbers, transaction amounts, business strategies, and competitive information.
The blockchain stores mathematical proofs instead of raw information. For example, the blockchain could store a proof showing that a borrower has been approved for a loan, without storing the borrower's name or the loan amount.
Step 2: Enable Selective Disclosure
Define rules for what data can be shared, with whom, and when. The organization creates policies that specify who can see what information. For example, a policy might specify that the tax authority can see transaction information related to tax compliance, but the tax authority cannot see information related to business strategy.
Allow compliance checks without exposing full transaction details. When a government agency requests information to verify compliance, the organization can show only the information that is required for compliance verification. The government agency does not receive information about other transactions or unrelated business activities.
Create time-limited access tokens. The organization can allow access to information for a limited period of time. For example, a government agency might receive access to transaction information for thirty days. After thirty days, access expires and the government agency can no longer view the information.
Step 3: Verify with Zero-Knowledge Proofs
Use cryptographic proofs instead of raw data. Rather than showing a transaction's details, show a mathematical proof that the transaction is valid. Validity is confirmed on-chain without revealing sensitive information. The blockchain verifies that the proof is correct. If the proof is correct, the transaction is accepted. If the proof is incorrect, the transaction is rejected.
Maintain security through cryptographic verification. Zero-knowledge proofs are mathematically secure. If someone tries to create a false proof, the fraud can be detected mathematically. This provides strong security without requiring anyone to examine transaction details.
Step 4: Support Secure Data Collaboration
Allow multiple parties to cooperate using proofs rather than shared databases. In situations where multiple organizations need to work together but cannot share sensitive information, zero-knowledge proofs enable cooperation. Each organization proves that it is following the rules without sharing raw information.
Enable trust without data leakage. Traditional collaboration requires sharing sensitive information in shared databases. This creates risk because the information could be leaked or stolen. Zero-knowledge proofs eliminate this risk. Organizations can verify each other's actions using proofs without sharing sensitive information.
For example, an international payment network could operate where each bank proves it has sufficient reserves using zero-knowledge proofs. Each bank does not need to share its financial details with other banks. Each bank can simply provide a proof showing it has sufficient reserves.
Step 5: Maintain Auditable Compliance
Generate regulator-ready audit proofs and reports while keeping confidential data shielded from public access. The organization maintains a complete record showing that all transactions followed regulatory requirements. Regulators can request audit proofs that demonstrate compliance.
Provide mathematical proof of compliance. Rather than showing transaction details, provide mathematical proofs that all transactions followed regulatory requirements. Regulators can verify these proofs mathematically without reviewing raw transaction data.
Preserve transaction owner's privacy. Because proofs are used instead of raw data, the transaction owner's privacy is protected. The regulator can verify compliance without learning details about the transaction owner's identity, transaction amounts, or business activities.
The Technical Checklist for Platform Selection
Deciding early between scale-first (zkSync) and privacy-first (Midnight) based on data visibility, execution, and compliance needs prevents late-stage redesigns. Late-stage redesigns are expensive and time-consuming. If an organization chooses the wrong platform and discovers the mistake after months of development, the organization must redesign its systems. This redesign costs time and money.
Factor 1: Data Visibility Requirements
The first evaluation criterion is clear and measurable. Determine what percentage of transaction data must be permanently visible on the blockchain.
zkSync fits public, auditable transactions. If more than fifty percent of your transaction data must be public, zkSync is appropriate. Your auditors and regulators need to see transaction details. zkSync's transparent records make auditing and compliance verification straightforward.
Midnight fits private data with selective disclosure. If more than fifty percent of your transaction data must stay private, Midnight is more suitable. Your organization needs to keep transaction details confidential while still allowing selective access for regulators.
Factor 2: Execution Model Compatibility
Execution model refers to how transactions are processed by the blockchain.
zkSync delivers high-throughput, EVM-compatible execution on Ethereum. EVM stands for Ethereum Virtual Machine. EVM-compatible means that smart contracts written for Ethereum can run on zkSync with little or no modification. If your organization already uses Ethereum, you can migrate to zkSync with minimal changes. This migration could take weeks of engineering work.
Midnight enforces privacy at the protocol level. This means that privacy protection is built into Midnight's fundamental design. If your organization is building new systems specifically for privacy, Midnight's architecture is well-suited. However, if you already have Ethereum systems, moving to Midnight requires significant rearchitecture.
Factor 3: Compliance Architecture Alignment
Compliance architecture refers to how the organization demonstrates that it follows government rules.
zkSync relies on off-chain compliance with transparent execution. Identity verification and Know-Your-Customer processes happen off the blockchain. On-chain transactions are fully transparent. Government agencies can inspect transaction histories directly. This approach works well for organizations whose regulators prefer transparent records.
Midnight enforces privacy and disclosure rules on-chain. Privacy protection and selective disclosure happen on the blockchain itself. Government agencies cannot inspect raw transaction data but can receive selective disclosure of specific information. This approach works well for organizations whose regulators require privacy protection.
Factor 4: Integration Surface Evaluation
Integration surface refers to how the blockchain platform connects with other systems and tools.
zkSync plugs into Ethereum tooling and decentralized finance rails. The Ethereum ecosystem includes many mature tools for wallet management, smart contract development, transaction analysis, and compliance monitoring. If you choose zkSync, you can leverage this existing ecosystem.
Midnight integrates with identity, policy, and regulated data systems. The Midnight ecosystem is smaller and focused on privacy-first applications. If you choose Midnight, you may need to build custom tools or work with a smaller set of specialized vendors. This is not necessarily a disadvantage. Specialized tools sometimes work better than general-purpose tools. However, you should be aware that the ecosystem is smaller.
Factor 5: Risk Profile Assessment
Risk profile refers to the main risks that your organization faces.
zkSync reduces cost and operational risk. Using zkSync, you can process transactions at lower cost and higher speed. This reduces operational risk. However, zkSync increases regulatory risk if your application requires data privacy. The public transparency of zkSync creates regulatory risk if you need to keep data private.
Midnight reduces regulatory and data-exposure risks. Using Midnight, you can process transactions while keeping sensitive data private. This reduces regulatory risk and data-exposure risk. However, Midnight increases operational risk if your application requires maximum throughput. Midnight cannot process as many transactions per second as zkSync.
How to Build a Hybrid Blockchain Using zkSync and Midnight

When Hybrid Architectures Are Necessary
Institutions no longer need to choose between scale and privacy. By combining zkSync and Midnight, organizations can run high-volume public settlement while keeping sensitive execution and compliance data confidential. A hybrid architecture uses both platforms, with each platform handling what it does best.
Step 1: Separate Workflows
The first step is analyzing your organization's workflows and identifying which processes require public scale and liquidity, such as payments and settlement, versus confidential execution such as identity, compliance, and sensitive logic.
Identify public settlement workflows. These are workflows where transactions must be public and fast. Examples include payments between organizations, final settlement of financial obligations, and public liquidity for buying and selling assets. These workflows benefit from zkSync's high throughput and low fees.
Identify confidential execution workflows. These are workflows where information must stay private. Examples include identity verification, Know-Your-Customer compliance, risk assessment, and sensitive transaction logic. These workflows benefit from Midnight's privacy protection.
A typical institutional workflow might look like this. A customer requests to make a payment. The payment goes through identity verification (Midnight) and compliance checking (Midnight). After verification and compliance checking, the payment is settled (zkSync). Settlement confirmation is returned for internal accounting (Midnight).
Step 2: Deploy Dual Layers
The second step is deploying contracts and systems on both platforms.
Run high-volume, public transactions on zkSync. The public settlement layer processes payments using zkSync's speed and low fees. Treasury teams monitor settlement on zkSync's transparent records.
Execute privacy-critical logic on Midnight using zero-knowledge enforcement. The confidential execution layer handles identity verification, compliance checking, and sensitive transaction logic on Midnight. This information remains private.
Step 3: Connect via Proofs and Messaging
The third step is creating communication channels between the two platforms.
Link the two layers using cryptographic proofs and secure message passing, not raw data transfers. The key design principle is that no raw personal data flows between platforms. Only cryptographic proofs and formal assertions flow across platform boundaries.
The Midnight layer creates proofs proving that a user is compliant and approved for a transaction. That proof goes to zkSync. The zkSync contract verifies the proof and executes the settlement. Settlement confirmation flows back to the Midnight layer for internal reconciliation.
Information flow architecture would work like this. User submits transaction through compliance-aware identity system running on Midnight. Midnight verifies the user is compliant and approved for the transaction amount. Midnight generates a zero-knowledge proof that proves the user is approved without revealing approval details. That proof is submitted to zkSync along with the transaction. The zkSync contract verifies the proof and executes settlement. Settlement confirmation flows back to Midnight for internal reconciliation.
Step 4: Align Compliance and Governance
The fourth step is deciding where compliance decisions and governance occur.
Expose zkSync activity publicly for auditability. Governance decisions and audit trails remain public on zkSync for transparency. When regulators request to see governance decisions or audit trails, the organization can point to the public zkSync records.
Use Midnight's selective disclosure for regulators and auditors. When government agencies request information, Midnight's selective disclosure mechanisms allow the organization to share specific information without exposing everything.
This creates a division of responsibility. Governance and audit are public on zkSync. Transaction execution details are private on Midnight. Compliance is verified on both layers through proofs that flow between them.
Step 5: Operate as One Stack
The fifth step is presenting the hybrid system to users and internal teams as a single unified system.
Present both layers as a single institutional system to treasury, risk, and operations teams with unified monitoring and controls. From the user perspective, this operates as a single blockchain. The underlying technical separation between public and private layers remains invisible to users.
Treasury systems see a single settlement interface. They submit a transaction and receive confirmation. The underlying system validates compliance on Midnight, generates proofs, submits settlement on zkSync, and returns confirmation to treasury. None of this complexity is visible to the treasury team.
Risk teams operate against unified dashboards. They monitor exposure and risk as if it were a single system. Compliance teams manage a single approval workflow. From their perspective, everything is integrated.
Real-World Use Cases

Midnight Privacy DApp Funding via Project Catalyst
The Midnight Foundation partnered with Cardano's Project Catalyst to launch a funding track for privacy-first applications called Compact DApps. These applications demonstrate real-world use of Midnight's privacy technology. The funding program has identified authentic use cases in multiple areas.
Digital identity systems are applications that verify who people are while keeping personal information private. Medical record management systems allow patients to control access to their medical information. Confidential voting systems allow people to vote while keeping their vote private. Business-to-business transaction networks allow organizations to work together while keeping business information confidential.
The existence of dedicated funding for privacy applications indicates that privacy is a genuine constraint for many organizations. Organizations are willing to invest significant capital to solve privacy problems. This shows that privacy is not an optional feature but a genuine business requirement.
NightSwap: Privacy-Preserving Decentralized Exchange on Midnight
A planned privacy-preserving Decentralized Exchange is being built natively on Midnight. NightSwap combines confidential trading with decentralized market-making access. A Decentralized Exchange, or DEX, is a platform that allows people to trade assets directly without a central organization controlling the trades.
Traditional decentralized exchanges on public blockchains expose all trading activity. Traders' positions are visible to everyone watching the chain. Market-making strategy is visible to everyone. This information leakage creates problems. Competitors can copy successful trading strategies. Large trades can move market prices if other traders see them coming.
A privacy-preserving decentralized exchange eliminates this information leakage. Traders' positions remain private. Trading strategy remains private. Market prices are not affected by large traders seeing information about other traders' positions. The fact that sophisticated decentralized finance teams are building on Midnight rather than Ethereum or existing Layer-2 platforms indicates that privacy is becoming a competitive differentiator, not a niche feature.
Tradable: 1.7 Billion Dollar Real-World Asset Tokenization
Tradable deployed and tokenized a 1.7 billion dollar private credit portfolio on zkSync Era. Tokenization means converting a real-world asset into a digital token on a blockchain. Private credit refers to lending money to organizations outside of traditional banks.
This deployment settled real institutional assets that subsequently traded with regulatory compliance. The value is genuinely significant. The deployment demonstrates that zkSync can handle sophisticated institutional asset management at scale. The choice of zkSync for this deployment shows why zkSync was appropriate for this use case.
Private credit portfolios require transparent settlement. Government agencies need to verify that settlements happened correctly. Public liquidity is necessary. Investors need to be able to buy and sell shares of the portfolio. Real-time settlement is important. When an investor buys or sells shares, the transaction must settle quickly so the investor knows the transaction is complete. Low operating costs are essential. The cost of settlement transactions must not exceed the profit margin on the investment.
zkSync's transparent settlement satisfies regulatory requirements. zkSync's high throughput satisfies liquidity requirements. zkSync's low fees satisfy cost requirements. The choice of zkSync for this deployment demonstrates that zkSync is appropriate for this use case.
Institutional Ecosystem Growth: Union Chain and Elastic Network
Union Fintech developed an institutional real-world asset-focused Layer-2 blockchain. This blockchain is specifically designed for institutions that want to tokenize real-world assets. Major deployments on this blockchain and similar platforms show enterprise-grade use of zkSync infrastructure for regulated applications.
These deployments manage billions of dollars in tokenized assets. The fact that these deployments exist and are handling real money shows that zkSync can handle sophisticated institutional asset management at scale. These are not experiments or pilots. These are production systems managing real assets and real value.
The Outlook for ZKSync vs Midnight
Institutions are moving away from general-purpose blockchains toward networks designed for specific business needs. General-purpose blockchains try to serve all use cases. This approach makes some compromises. Scale-optimized layers like zkSync support high-volume settlement. Privacy-first chains like Midnight address regulatory and data-protection requirements. Specialized platforms serve specific needs better than general-purpose platforms.
Emergence of Hybrid Architectures
Rather than choosing one network, institutions will combine multiple layers. Public settlement and liquidity will run on zkSync. Confidential execution and compliance workflows will operate on Midnight. This hybrid approach takes advantage of the strengths of both platforms.
The emergence of hybrid architectures shows that blockchain technology is maturing. Early blockchain development treated all uses as variations on the same fundamental problem. Modern institutional use recognizes that different business models have different needs. Different needs require different technical solutions.
From Pilots to Production
Clear separation of scale and privacy reduces regulatory friction. Government agencies understand why certain information is public and certain information is private. Shortened approval cycles result. Organizations do not need to negotiate with government agencies about why transparency is necessary or why privacy is required. Acceptance of the platform is accelerated because the technical design matches the organization's actual needs.
Enterprise blockchain deployments move from experimentation into sustained production use. Organizations that correctly identify their constraints and select appropriate platforms move to production faster. Organizations that have clear regulatory approval move to production faster. Organizations that have tested their systems thoroughly move to production faster.
FAQ
1. How do we decide between zkSync and Midnight for our business?
The decision depends on your primary constraint: scale and cost (zkSync) or privacy and regulatory exposure (Midnight). Choosing early prevents costly redesigns and failed pilots.
2. When does zkSync make the most business sense?
zkSync is best for high-volume, low-cost, public transactions such as payments, settlement, exchanges, and fintech platforms where transparency and speed matter more than confidentiality.
3. When is Midnight the better choice?
Midnight is suited for regulated and sensitive workflows where data privacy, selective disclosure, and zero-knowledge compliance are mandatory—even at the expense of throughput and higher fees.
4. What happens if we choose the wrong platform?
A mismatch increases regulatory risk, integration complexity, and rework costs, often leading to delays and failed pilots. Institutions typically lose 20–40% in time and budget correcting late-stage decisions.
5. Do institutions need to choose only one chain?
No. Many institutions adopt a hybrid architecture—using zkSync for public settlement and Midnight for private compliance—balancing scale, cost efficiency, and regulatory protection.
How TokenMinds Guides Your Blockchain Selections
Selecting the incorrect blockchain can result in pilot failures, significant rework costs and delays in obtaining regulatory approvals. TokenMinds provides a service that enables institutions to select the appropriate blockchain by ensuring alignment of their business goals, regulatory compliance requirements and technical specifications prior to committing significant capital.
TokenMinds guides blockchain selection by first assessing business and regulatory needs, then evaluating technical fit to determine whether zkSync, Midnight, or a hybrid approach is optimal, followed by designing a low-risk pilot to validate performance and compliance, and finally delivering a clear roadmap to move confidently from pilot to production.
Conclusion
Institutions separate Scale and Privacy via public settlement with confidential execution. zkSync provides scalable auditing of transactions for settlement while Midnight achieves data privacy for users utilizing a privacy-centric approach. The separation of scalable, compliant workflow architecture from a privacy-first workflow architecture enables institutions to achieve Compliant Growth with no architectural trade-off.
Schedule a complimentary consultation with TokenMinds to assess how your institution should balance transaction scale and data privacy, and to evaluate whether zkSync or Midnight is the right infrastructure for your payment and settlement workflows—without disrupting your existing financial systems.








